Enterprise Security (ES)
Home » Security License » Splunk » Security » Enterprise Security (ES)
Splunk ES APP
Splunk’s suite of network and security solutions allows companies to implement a comprehensive security solution while monitoring traffic exchanged across the network. Splunk (Splunk Enterprise Security), abbreviated as Splunk ES, is an advanced, extensible and functional technology that indexes and searches files registered in a system. The Splunk ES APP tool can analyze data by intelligent algorithms and provide businesses with an efficient action plan.
In addition to building a security strategy based on continuous analysis and monitoring of today’s threats, Splunk ES allows organizations to implement an optimized security solution with minimal response time that focuses on the information exchanged by clients.
By relying on machine learning to identify threats, Splunk ES allows organizations to make more accurate decisions about threats. The licensed Splunk ES APP tool is just one of several efficient solutions offered by Splunk.
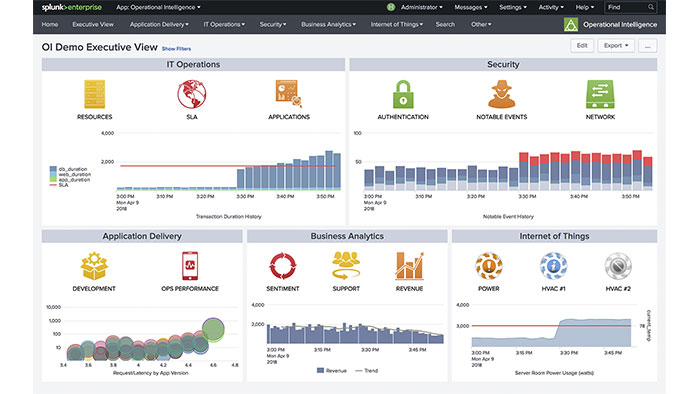
The company’s intelligent solutions are mainly related to the search, monitoring and analysis of big data generated by machines through a web-based user interface. Splunk ES helps security professionals accomplish their tasks by capturing, indexing, and displaying real-time data relationships in a searchable environment and providing charts, reports, alerts, and dashboards. The use of Splunk is not limited to big data management, and security experts can use this technology in various ways, one of which is the implementation of a network security operation center.
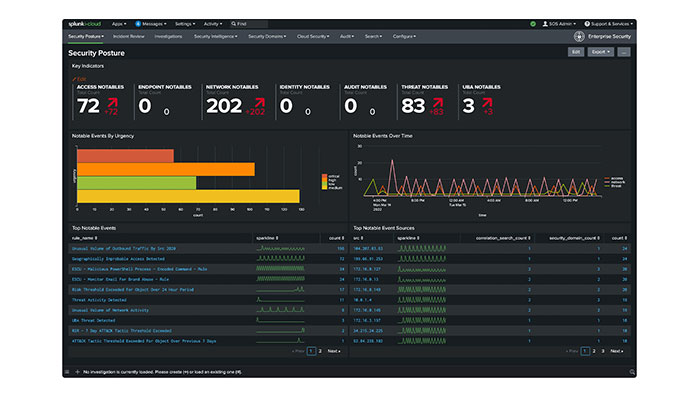
Splunk Enterprise Security
The security professional has visibility into security-relevant threats present in today’s enterprise infrastructure thanks to Splunk Enterprise Security. Users can capture, monitor, and report on data from security devices, systems, and applications using the search and correlation capabilities of Splunk Enterprise Security, which is based on the Splunk License operational intelligence platform.
As problems are found, security analysts can look into and address security threats quickly in the access, endpoint, and network protection domains. Using the Splunk Security Incident and Event Management (SIEM) platform, enterprise security can be managed. In plain English, it contains everything in Security Essentials but also adds the capacity to manage events according to risk, the capacity to perform deep security data correlations, and other beneficial features like SOC automation. (It means you can programmatically close a firewall port if Splunk detects a DDOS attack on one on an open port.
Benefits of using the Splunk Enterprise Security
One of the most important advantages of Splunk Enterprise Security is performance, expandability and providing creative solutions for collecting and presenting data. Of course, working with Splunk is not easy and requires experience and expertise. In general, the main advantages of these solutions, especially Splunk ES APP, can be mentioned as follows:
- Experts can use Splunk ES to create analytical reports with interactive charts and tables and share them with other parts of the organization.
- By intelligently analyzing the data generated by security technologies, Splunk ES can help security experts adopt powerful rules and policies to respond to threats.
- Providing functional capabilities related to alert management, dynamic threat detection and detection, accurate data search, and advanced threat analysis.
- Providing a flexible solution in the field of customizing searches, alerts, reports and dashboards according to user needs with the aim of continuously monitoring network traffic.
- Implementation of an efficient security operations center for rapid response to incidents
- Splunk solutions are scalable and flexible.
- Splunk’s suite of solutions automatically identify and highlight useful information and links in data. So you don’t have to do it manually. The above approach reduces the time spent on searches and simplifies the information labeling process.
Analytics-based security
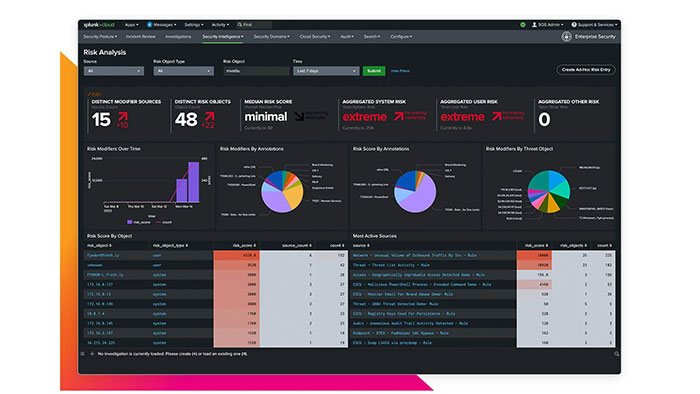
The process of identifying and correlating security data with each other (information related to IT infrastructure, security products, and data generated by clients) and quickly adapting this information to provide an accurate threat perspective is called analytics-based security. The licensed Splunk ES APP tool allows businesses to quickly identify and respond to internal and external threats by providing an analytics-driven SEIM solution. Here are some of the most important uses of Splunk ES:
Quick investigation and handling of threats
To accelerate the threat detection process, Splunk ES provides case-based search as well as visual, dynamic and static communication so that security experts can quickly identify malicious activity. In this context, Splunk ES APP tool examines all the data generated in the network in order to identify threats based on their behavior patterns. and provide more information to security experts by tracking hackers’ actions and examining evidence.
Prioritizing events and responding appropriately to them
Analysts and security teams can use alerts and events, anomalies related to User Behavior Analytics (UBA), generated reports related to the state of network traffic, and the like for faster and more transparent responses.
Continuous monitoring of the security situation
Splunk ES provides a complete set of predefined dashboards such as Key Security Indicators (KSI), Key Performance Indicators (KPI), Dynamic and Static Tolerance Thresholds, and Trending Indicators to provide a comprehensive and clear picture of the organization’s security status.
Difference Between Splunk Security Essentials and Splunk ES
The goals and intentions of these two solutions diverge significantly. Sadly, a lot of people confuse these two solutions. Foundational Security Use Cases can be found in Splunk Security Essentials, a free security reference app on Splunkbase. Among other helpful categorizations, Security Essentials’ great feature is the organization of all use cases into stages.
The degree of search complexity can change between the aforementioned stages. As you advance, you’ll observe the transition from straightforward data gathering and aggregation to complete threat feed integration. The Risk Framework, which modifies the risk score based on the involved asset, makes a lot of this possible within Core Splunk if you have Enterprise Security.
The Security Incident and Event Management (SIEM) platform from Splunk is called Splunk Enterprise Security. In the simplest terms, Splunk Enterprise Security finds patterns in your data and uses correlation searches to analyze events in a way that is security-relevant. Additionally, Splunk creates a thorough view of enterprise security risk by comparing the identified event to the assets and asset value in your environment.
Other beneficial features of Splunk Enterprise Security include Incident Review, Investigation Management Tools, and etc. These other features are not discussed in this article. The statistical analysis of data is an intriguing feature of Splunk Enterprise Security. Splunk Enterprise Security can identify specific security events as well as statistical departures from your baseline data for the purpose of conducting security investigations and generating security alerts. Over time, as you become more familiar with your data and have had a chance to observe the unusual security events, it will start to influence how you tune and optimize Enterprise Security for the greatest benefit of expedited investigation and security alerting.