User Behavior Analytics (UBA)
Home » Security License » Splunk » Security » User Behavior Analytics (UBA)
Splunk UBA
Splunk User Behavior Analytics technology, or Splunk UBA for short, is used to analyze the behavior of users in the network. It has many capabilities. Here are some of the most important ones:
- It has a simple interface for SOC analysts, event reviewers and SEIM managers.
- Using Splunk UBA and its licenses, it is possible to identify cyber-attacks and internal threats.
- Increases the effectiveness of restorative processes by prioritizing threats and avoiding false positive assessments.
In general, complex cyberattacks are always covert and difficult to detect, which is why it is so important to identify them and ways to infiltrate and eliminate their threats to protect confidential data. This means that the task of security teams at present is to identify and eliminate hidden threats on the network, regardless of any other issues.
The Splunk UBA process of user behavior analysis helps companies and organizations to identify known, unknown, and hidden threats through machine learning, similar group analysis, and advanced correlation. Splunk UBA license, in addition to overseeing the security analysis process, requires minimum management measures and integrates with existing infrastructure. Identify hidden threats.
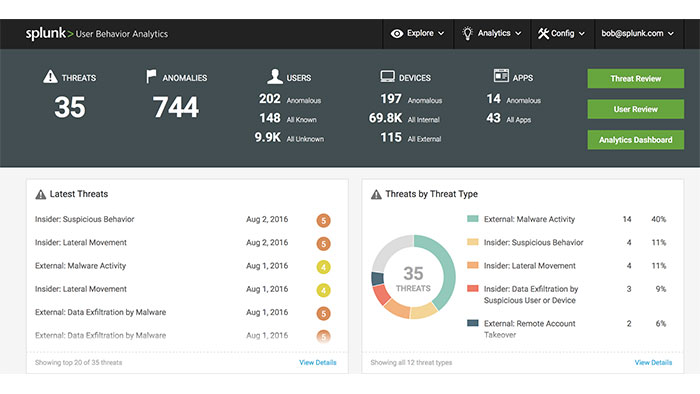
The licensed Splunk User Behavior Analytics (UBA) APP is a machine learning-based solution that helps organizations discover unknown threats and anomalous behavior and solves a wide range of use cases to detect internal threats and external attacks. It uses unsupervised machine learning algorithms to generate risk assessments and actionable findings, along with supporting evidence that improves how Security Operations Center (SOC) analysts can respond faster. It also provides visual cues for security analysts and threat hunters to proactively investigate unusual behavior.
Specific methods in identifying threats
The identification process in this software is based on machine learning methods that do not require human analysis and allows behavioral profiling and analysis of similar groups for users, equipment, user accounts of services and applications. As a result, threats and anomalies are automatically and accurately identified. Tests related to the prevention, detection and removal of network-related security problems should be integrated through continuous monitoring as well as advanced analysis.
Note that Splunk Enterprise, Splunk Enterprise Security, and Splunk UBA can work together to provide the following capabilities:
- It is possible to develop Search, Pattern, Expression-based approaches in Splunk Enterprise and Splunk ES to find complex Kill Chain illustrations.
- Security hole detection techniques provide statistical profiling for the security team. This makes it easy to use large-scale data available in Splunk Enterprise.
- By combining machine learning methods and advanced analytics capabilities with these softwares, organizations can perform activities such as network monitoring, alerting, sharing, and identifying known and unrecognized threats, regardless of the size of the organization or their skill set.
Identify hidden threats
Splunk UBA software, among the millions of anomalies it has observed on the network, identifies several major threats and speeds up the process of reviewing and providing solutions. It uses security-based algorithms for machine learning, dynamic statistical methods as well as correlations to identify hidden threats without human analysis. False Positives can also be reduced by being aware of concepts, situations, and content.
Identify Kill Chain and Attack Vector
This technology detects abnormalities and Kill Chain attacks. It also detects malware add-ons or malicious internal replications and responds to real-time signs for abnormal actions (such as suspicious URLs or Land-Speed Login violations).
Splunk UBA architecture and implementation
Splunk UBA includes the Hadoop ecosystem. This ecosystem is used for open, cost-effective and scalable open data. This technology is designed to analyze events on a large scale and in real time. These events include graph databases that are used to process and establish secure communications on the network. Splunk UBA is approved for scaling hundreds of terabytes and billions of events and can be implemented as software on-premise, on virtual devices, or as a Public Cloud Instance with customer management.
Uses of Splunk UBA in network
Splunk UBA has been able to provide the most compelling security analysis solution in recent years by providing the full details of an attack (cyber-attack or intra-organizational threat as well as providing a platform for detection, response and automation).
IP Theft and Data Exfiltration
This software can identify evidence of unauthorized transfer of data in the organization from assets or users.
Prevent hacking of accounts
This software quickly identifies vulnerable user accounts and provides a complete view of threats related to the Privileged Account.
Virtual Cloud Asset and Container
It can perform the process of determining behavioral principles, detecting abnormalities, and identifying threats for virtual containers and cloud applications.
Detect and identify Internet scams
Behavioral modeling of transactions and automated threat modeling to identify fraud-related activities.
Identify suspicious behavior of users and applications
Identify threats and anomalies related to users and institutions of an organization with behavioral analysis of the institution and user (UEBA)
Malware detection
Ability to detect cyber-attacks and get an overview of the threat situation within the organization
Splunk UBA and behavioral analysis
The licensed Splunk UBA can detect cyber-attacks and intra-organizational threats using behavioral principles, data science, machine learning, and similar group analysis. With advanced security analysis, this solution enables organizations of all sizes and skills to identify and respond to known, unknown and hidden threats. Splunk continues to provide the most compelling security analysis solution in the IT industry by detailing the step-by-step cyber-attack or internal threat.
Splunk UBA
Splunk User Behavior Analytics technology, or Splunk UBA for short, is used to analyze the behavior of users in the network. It has many capabilities. Here are some of the most important ones:
- It has a simple interface for SOC analysts, event reviewers and SEIM managers.
- Using Splunk UBA and its licenses, it is possible to identify cyber-attacks and internal threats.
- Increases the effectiveness of restorative processes by prioritizing threats and avoiding false positive assessments.
In general, complex cyberattacks are always covert and difficult to detect, which is why it is so important to identify them and ways to infiltrate and eliminate their threats to protect confidential data. This means that the task of security teams at present is to identify and eliminate hidden threats on the network, regardless of any other issues.
The Splunk UBA process of user behavior analysis helps companies and organizations to identify known, unknown, and hidden threats through machine learning, similar group analysis, and advanced correlation. Splunk UBA license, in addition to overseeing the security analysis process, requires minimum management measures and integrates with existing infrastructure. Identify hidden threats.
The licensed Splunk User Behavior Analytics (UBA) APP is a machine learning-based solution that helps organizations discover unknown threats and anomalous behavior and solves a wide range of use cases to detect internal threats and external attacks. It uses unsupervised machine learning algorithms to generate risk assessments and actionable findings, along with supporting evidence that improves how Security Operations Center (SOC) analysts can respond faster. It also provides visual cues for security analysts and threat hunters to proactively investigate unusual behavior.
Specific methods in identifying threats
The identification process in this software is based on machine learning methods that do not require human analysis and allows behavioral profiling and analysis of similar groups for users, equipment, user accounts of services and applications. As a result, threats and anomalies are automatically and accurately identified. Tests related to the prevention, detection and removal of network-related security problems should be integrated through continuous monitoring as well as advanced analysis.
Note that Splunk Enterprise, Splunk Enterprise Security, and Splunk UBA can work together to provide the following capabilities:
- It is possible to develop Search, Pattern, Expression-based approaches in Splunk Enterprise and Splunk ES to find complex Kill Chain illustrations.
- Security hole detection techniques provide statistical profiling for the security team. This makes it easy to use large-scale data available in Splunk Enterprise.
- By combining machine learning methods and advanced analytics capabilities with these softwares, organizations can perform activities such as network monitoring, alerting, sharing, and identifying known and unrecognized threats, regardless of the size of the organization or their skill set.
Identify hidden threats
Splunk UBA software, among the millions of anomalies it has observed on the network, identifies several major threats and speeds up the process of reviewing and providing solutions. It uses security-based algorithms for machine learning, dynamic statistical methods as well as correlations to identify hidden threats without human analysis. False Positives can also be reduced by being aware of concepts, situations, and content.
Identify Kill Chain and Attack Vector
This technology detects abnormalities and Kill Chain attacks. It also detects malware add-ons or malicious internal replications and responds to real-time signs for abnormal actions (such as suspicious URLs or Land-Speed Login violations).
Splunk UBA architecture and implementation
Splunk UBA includes the Hadoop ecosystem. This ecosystem is used for open, cost-effective and scalable open data. This technology is designed to analyze events on a large scale and in real time. These events include graph databases that are used to process and establish secure communications on the network. Splunk UBA is approved for scaling hundreds of terabytes and billions of events and can be implemented as software on-premise, on virtual devices, or as a Public Cloud Instance with customer management.
Uses of Splunk UBA in network
Splunk UBA has been able to provide the most compelling security analysis solution in recent years by providing the full details of an attack (cyber-attack or intra-organizational threat as well as providing a platform for detection, response and automation).
IP Theft and Data Exfiltration
This software can identify evidence of unauthorized transfer of data in the organization from assets or users.
Prevent hacking of accounts
This software quickly identifies vulnerable user accounts and provides a complete view of threats related to the Privileged Account.
Virtual Cloud Asset and Container
It can perform the process of determining behavioral principles, detecting abnormalities, and identifying threats for virtual containers and cloud applications.
Detect and identify Internet scams
Behavioral modeling of transactions and automated threat modeling to identify fraud-related activities.
Identify suspicious behavior of users and applications
Identify threats and anomalies related to users and institutions of an organization with behavioral analysis of the institution and user (UEBA)
Malware detection
Ability to detect cyber-attacks and get an overview of the threat situation within the organization
Splunk UBA and behavioral analysis
The licensed Splunk UBA can detect cyber-attacks and intra-organizational threats using behavioral principles, data science, machine learning, and similar group analysis. With advanced security analysis, this solution enables organizations of all sizes and skills to identify and respond to known, unknown and hidden threats. Splunk continues to provide the most compelling security analysis solution in the IT industry by detailing the step-by-step cyber-attack or internal threat.
A class of software called user behavior analytics (UBA), also known as user entity behavior analytics (UEBA), aids security teams in spotting and countering insider threats that might otherwise go unnoticed. The licensed UBA tracks the behaviors of threat actors as they move through enterprise environments using machine learning and analytics, putting data through a number of algorithms to find actions that deviate from user expectations.
The licensed UBA is a valuable tool for spotting suspicious patterns that may indicate credential theft, fraud, and other malicious activity because insider threats are the most difficult to detect and potentially dangerous ones.
Among the various threat categories are:
- Change in access credentials is a form of privilege escalation.
- Abuse of privileged accounts: unauthorized use of access rights.
- The stealthy takeover of accounts for malicious purposes is known as credential compromise.
- Exfiltration of data is the theft of private, sensitive, and confidential information within an organization by malware or an intruder.
- Unusual behavior includes accessing external domains, remotely accessing highly privileged resources, and unusual login duration, time, or location.
What distinguishes the UBA from the UEBA?
Analyzing user behavior is very similar to analyzing user and entity behavior. The “entity” component, which inspired Gartner to coin the term “UEBA,” is also covered by most UBA solutions. However, UEBA is arguably the more popular term because it clearly distinguishes between user and entity behavior. Through the use of multidimensional behavior baselines, dynamic peer group analysis, and unsupervised machine learning, the licensed Splunk UEBA tool (also known as “UBA”) assists organizations in battling insider threats.
Splunk UBA Order Pricing
Customers can order various Splunk software and licenses by contacting our sales specialists at Golicense.net.
Splunk UBA License
Customers are able to get more information about different Splunk licenses from our sales specialists.
Splunk UBA Order Pricing
Customers can order various Splunk software and licenses by contacting our sales specialists at Golicense.net.
Splunk UBA License
Customers are able to get more information about different Splunk licenses from our sales specialists.