SD-Access
Home » Cisco License » Solution » SD-Access
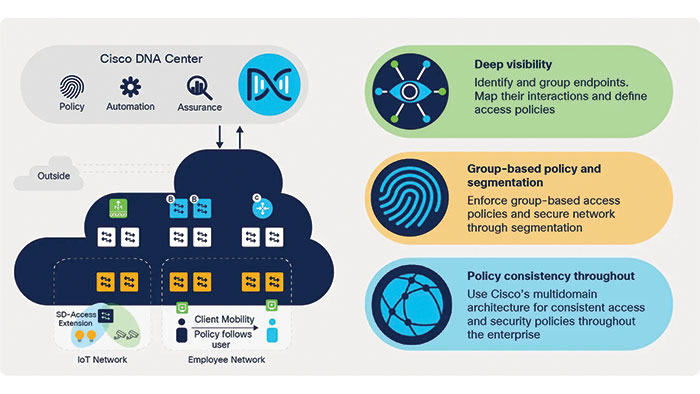
Cisco SD-Access
Cisco Software-defined Access or Cisco SD-Access takes the complexity out of your network. So network administrators can ease their minds. Cisco SD-Access offers end to end segmentation, network automation, consistent user experience without compromising the security and it provides a transformational shift in building and managing networks faster, easier and with improved business efficiency.
In SD-Access there are four key technologies, that make up this solution, each performing distinct activities in different network planes of operation:
- Control Plane—Messaging and communication protocol between infrastructure devices in the fabric.
- Data Plane—Encapsulation method used for the data packets.
- Policy Plane—Used for security and segmentation.
- Management Plane—Orchestration, assurance, visibility, and management.
In SD-Access the control plane is based on LISP (Locator/ID Separation Protocol), the data plane is based on VXLAN (Virtual Extensible LAN), the policy plane is based on Cisco TrustSec, and the management plane is enabled and powered by Cisco DNA Center.
SD-Access Fabric
A fabric is simply an overlay network. Overlays are created through encapsulation, a process which adds additional header(s) to the original packet or frame. An overlay network creates a logical topology used to virtually connect devices that are built over an arbitrary physical underlay topology.
In an idealized, theoretical network, every device would be connected to every other device. In this way, any connectivity or topology imagined could be created. While this theoretical network does not exist, there is still a technical desire to have all these devices connected to each other in a full mesh.
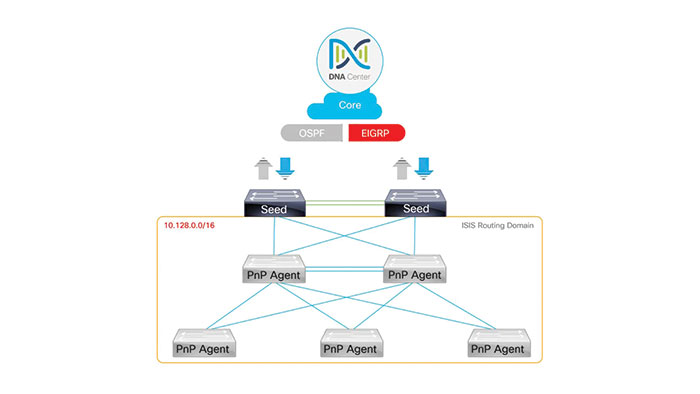
SD-Access Underlay
The underlay network is defined by the physical switches and routers that are used to deploy the SD-Access network. All network elements of the underlay must establish IP connectivity via the use of a routing protocol. The SD-Access network underlay focuses on transporting data packets to network devices for the overlay network. You can use Cisco DNA Center to automate user access policy and apply the right policies for users or devices to any application across the network.
Software-defined access via DNA center offers an intuitive GUI experience to automate everyday tasks such as network configuration provisioning and troubleshooting. This results in improved resolution of issues, reduce time for Network adaptation and reduced security breaches. Software-defined access networks consist of a software underlay and a fabric overlay.
The SD-Access underlay network consists of your network devices and the protocols they use to communicate with each other. The prerequisite is to ensure that you’ve completed the required configurations on your seed devices so that they can communicate with Cisco DNA Center. The configurations may differ with each version of DNA Center so refer to the documentation for the configurations for your version.
SD-Access Overlay
SD-access overlay is one of three key components of the software-defined access or SD-Access technology along with the other two components, SD-Access underlay and SD access. Policy overlay provides the infrastructure for building virtual networks with policy based segmentation constructs and provides dynamic host services for mobility and enhanced security that go far beyond the normal switching and routing capabilities.
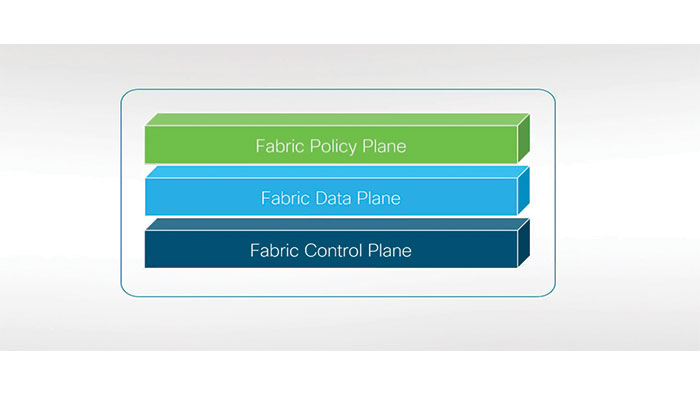
Building blocks that make up SD-Access overlay SD access is fabric overlay or simply overlay which is the logical virtualized topology that is built on top of the network’s physical underlay. The fabric overlay consists of three key building blocks, the fabric control plane, the fabric data plane and the fabric policy plane.
The fabric control plane is a logical mapping and resolving of users and devices that are associated with virtual extensible LAN or VXLAN tunnel endpoints. The mapping and resolving activities are performed using the locator ID separation protocol or a LISP. The fabric data plane is a logical overlay created by packet encapsulation using VXLAN with the group policy option or GPO VXLAN.
GPO offers several advantages for SD access, include support for both layer 2 and layer 3 virtual topologies, the ability to operate over any IP based network with built in network segmentation using virtual routing and forwarding and our virtual networks, the use of scalable group tags or SGTs.
Finally, the fabric policy plain is where your business intent is translated into a network policy. This is done using address agnostic SGTs and group based policies. The fabric policy plain uses Cisco’s TrustSec technology with the SGTs to provide security. Together these building blocks form the core of what powers the SD-access overlay. It is also what makes the overlay virtually interconnect all the network devices to form a fabric and remove the complexities and limitations of the physical underlay.
SD-Access Underlay Automation
With Cisco DNA Center you can design provision and manage your underlay network by automating the discovery and provisioning of new devices. Underlay automation speeds up the process of building SD-Access underlay networks. So by taking traditional network planning and implementation processes out of the picture and after you have completed all the prerequisites you can begin automating your network underlay.
You can begin by adding your primary and secondary seat devices to your DNA center inventory and then DNA center automatically discovers system information and prepares the seed devices for underlying network discovery and automation.
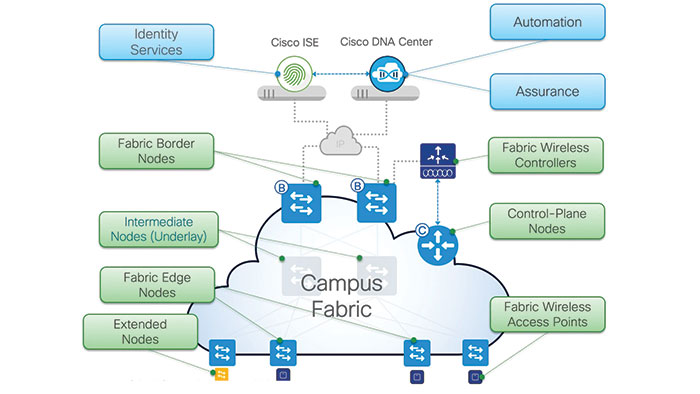
SD-Access Topology and Components
In the fabric environment, the Cisco DNA Center is responsible for the automation and acts as an orchestration engine which provides the GUI management. After that, Cisco DNA assurance as a part of the DNA center, collects information about the network, such as SNMP, Syslog, NetFlow and streaming telemetry artistic samples. Then, it combines this information with contextual data related to the devices, such as quality, DNS, AAA, inventory, location and etc. Cisco DNA assurance correlates and uses the machine learning to provide meaning from these amount of information flowing from the network.
As part of DNA Center, assurance provides a unique network insights using the correlation provided by the analytics engine and that contextual data which is collected from DNA center helping you quickly find the root cause of problems on your network and provides much faster remediation steps to resolve the issue.
Cisco ISE is your identity services engine which plays a critical role in the Cisco SD-Access solution on the front end, providing a link between customer’s identities, devices they are using, their location and their access method to the network. This information is critical for establishing trust and security within the network and beyond the onboarding process.
The policy application within the DNA center controller enables the simple and easy-to-understand meaningful representation for crafting and managing executing policy by Cisco ISE. Moreover, the built contextual awareness between user groups and access permissions can be tied into DNA assurance providing a comprehensive view of users, devices and applications in a way that hasn’t been possible before.
Control plane nodes, in this topology, contain the settings protocols and tables to provide the endpoint to the location mapping system for the fabric overlay. Their role is to keep track of endpoints and their associated connectively.
Fabric border contains settings, protocols and tables to provide internal and external routing between the fabric overlay and the outside networks and border nodes is the exit and the entry point to the fabric providing all external connectivity.
Fabric edge nodes contain the settings, protocols and tables to provide wired endpoint onboarding and host mobility for the fabric overlay. The fabric edge nodes act as the security point and all traffic that enters or leaves the fabric from the edge he secured at this point.
Edge nodes are where the clients connect to the fabric and keep track of the clients attached to them, update the control plane node about the changes to the attacks to clients and cache information about connections to clients associated with other fabric edge nodes or the border.
Fabric wireless controller is responsible for connecting the fabric access points and wireless endpoints to the SD-access fabric.