Cisco Firepower 4100 and Firepower 9300 Overview
As Cisco has introduced its next-generation firewalls (NGFW) and in this article we are going to take a look on these products and see what are their main architectures, features and capabilities.
Essentially, it is important to know what is the NGFW should provide?
First of all, we expect a NGFW device like Cisco Firepower 9300 to provide a Modular Chassis in order to system hardware components can be upgraded independently. Secondly, its architectural scale should leverage the best of security processing components (x86, NPU, Crypto) and scale with Clustering.
Moreover, the device should have no Single Failure Point meaning that all hardware and software components are redundant and as independent as possible. Furthermore, the NGFW platform should provide the same benefits in physical, virtual, and hybrid SDN environments.
Also, one of the biggest expectations is that the services should be added, removed, upgraded, and modified without disrupting existing flows providing Rapid Inline Changes. Finally, NGFW devices should support dynamic service chaining based on policy and context, open architecture to quickly add new services as market evolves and full automation through REST API enabling monitoring functions.
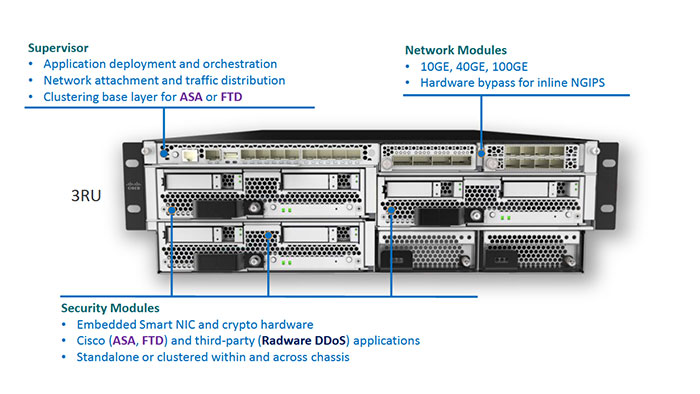
Cisco Firepower 9300 chassis overview
Now let’s take a look at the Cisco’s most powerful Firepower 9300 chassis overview in the following figure:
Cisco Firepower 9300 supervisor module
The Cisco Firepower 9300 supervisor module provides network interface allocation and security module connectivity, LACP or Static (in FXOS 2.4.1) Port-Channel creation with up to 16-member port, up to 500 VLAN sub interfaces for Container instances in FXOS 2.4.1 and clustering infrastructure for supported applications. You can also inspect its supervisor module in the below figure:
On the Cisco Firepower 9300 Smart Licensing is available for entire chassis. All product instances could be registered online, on the Cisco Smart Software Management website. Also, Cisco Firepower 9300 PLR license (Permanent license reservation) can be used in order to activate all premium features on the device permanently and without any Internet connection.
PLR licenses would be applied on the Firepower Management Center service in the first place. After that all devices that will be added on the FMC would be activated permanently.
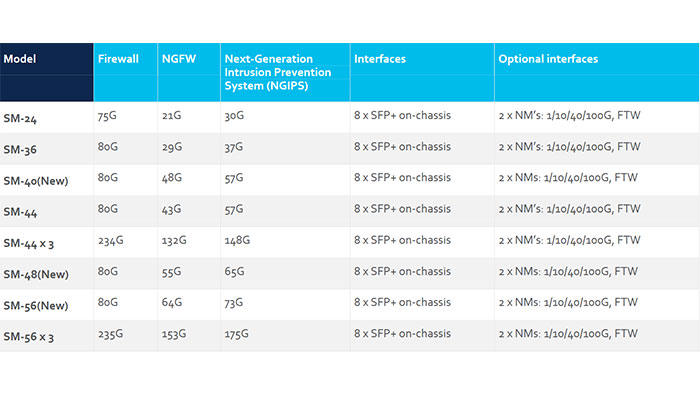
Firepower 9300 Security Modules
Firepower 9300 Security Modules provide dual 800GB SSD in RAID1 by default, Built-in Hardware Smart NIC and Crypto Accelerator. Plus, it supports IPSec/TLS VPN connection acceleration and transit TLS inspection with FTD 6.2.3+. You can find Cisco Firepower 9300 Security Modules summery in the following chart:
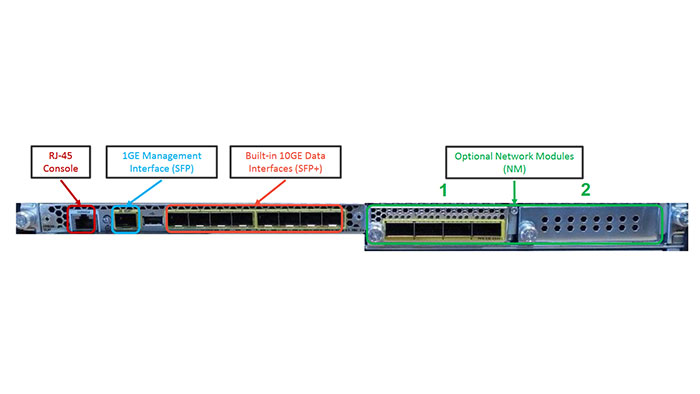
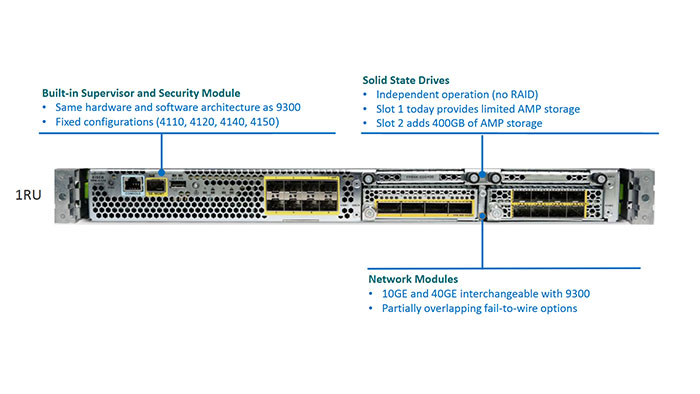
Cisco Firepower 4100 overview
Basically, the Cisco Firepower 4100 is Designed and optimized for FTD application however it supports ASA application as well. Its Data Plane runs on integrated NPU and Crypto module and threat-centric Advanced Inspection Modules run on x86 processor. Now let’s take a look at the Cisco Firepower 4100 overview in the following figure:
Firepower 9300 and 4100 with FTD Multi-Instances
Multi-instance capability lets you run container instances that use a subset of resources of the security module/engine. Multi-instance capability is only supported for the Firepower Threat Defense; it is not supported for the ASA. This feature is only supported on the FPR 9300/4100 with FTD.
The Firepower chassis includes a supervisor and up to three security modules on which you can install logical devices. A logical device helps you run one application instance (Firepower Threat Defense or ASA).
When you add a logical device, you also define the application instance type and version, assign interfaces, and configure bootstrap settings that are pushed to the application configuration. The application type determines whether you can run a single instance (native) or multiple instances (container).