Identity Manager Plus is an essential component of an organization’s infrastructure that specializes in identity and access management (IAM) to enhance security by efficiently managing user identities, access permissions, and security policies. This is achieved through automated user provisioning, strong authentication implementation and regulatory compliance. In parallel, the ManageEngine Identity Manager Plus License plays an important role in access control and enterprise security.
ManageEngine Identity Manager Plus License
It is normal for an organization to use a lot of software to meet its business needs. This means employees have to remember lots of passwords and log into apps multiple times a day. This can be tedious for users and admins. Administrators also face the daunting task of controlling access to these applications to ensure security. The licensed ManageEngine Identity Manager Plus Cloud is a cloud-based enterprise single sign-on service that provides users with secure, one-click access to business applications. Users only need to sign in once to access all of their apps.
ManageEngine Identity Manager Plus key features
- Access management: Ensure the right people have access to the right apps by assigning and revoking app access to users in bulk.
- Reports and Analytics: View comprehensive reports detailing when a specific user accessed an application. Monitor admin activity with a unique report detailing changes made to directories, users, and applications.
- User Lifecycle Management: Automate user lifecycle management by provisioning and deprovisioning users across different applications and services using cross-domain identity management (SCIM) system.
- Enterprise SSO: Provide one-click access to enterprise applications by enabling SSO. With Enterprise SSO, users can access all of their enterprise applications with a single click by signing in once with a set of credentials.
Supported Directories
Identity Manager Plus offers out-of-the-box integrations with the following directories and applications:
- Slack
- Zendesk
- Salesforce
- Zoho Directory
- G Suite Directory
- Azure Active Directory (AD)
You can also add users from the import section manually from other directories or systems, including local AD. This makes it easy to give users access to the applications they need.
Supported Applications
Identity Manager Plus supports any application (cloud-based or on-premises) that is SAML, OAuth, or OpenID Connect enabled. If you have a custom application that supports one of these protocols, it can be configured for SSO in Identity Manager Plus.
Dashboard
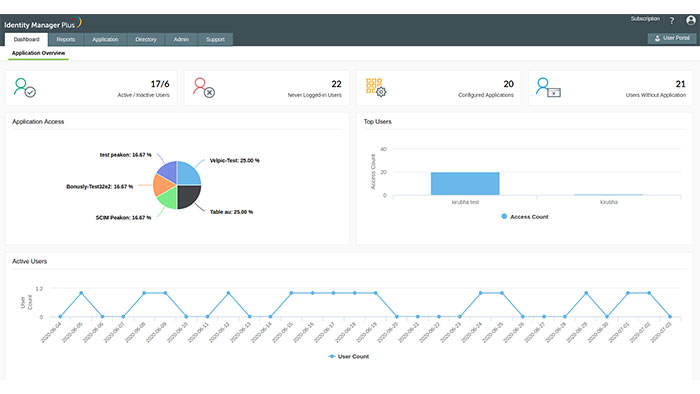
When you log in to Identity Manager Plus as an administrator, the Dashboard is the first page you see. The dashboard displays key metrics related to users and apps in easy-to-read graphical charts, including:
- Most Used Apps
- Never Signed In Users
- Active and Inactive Users
- Top and Worst Users plus
- Users without App Access
SAML SSO
Security Assertion Markup Language (SAML) is an open standard that combines authentication and authorization services with protected access resources. The licensed ManageEngine Identity Manager Plus supports the widespread and secure industry standard SAML 2.0. Identity Manager Plus SAML SSO eliminates the need for multiple user IDs and passwords, streamlines the user login experience, and improves security.
In SAML authentication, we have an Identity Provider (IdP) and a Service Provider (SP). The IdP verifies the user’s credentials and submits a claim to the SP as proof of verification. Here the IdP is Identity Manager Plus and the SP is the application or cloud service that a user wants to access.
How SAML works
There are two types of flows in SAML SSO.
SP Initiated SSO
- A user is attempting to log in to the SP.
- The user is redirected to the Identity Manager Plus login page. The user enters their directory credentials here.
- Identity Manager Plus verifies the user’s login and, if successful, issues an authentication claim that is sent to the SP along with the redirect link to the SP. The claim does not include the password. It has other personal attributes like last name, first name, email address and more.
- The SP accepts this claim after verifying the digital signature of the IdP and logs in the user.
IdP-initiated SSO
- A user logs in to the Identity Manager Plus portal.
- The SP accepts this claim after verifying the IdP digital signature and logs in as a user.
- To access an application, simply click on the appropriate application icon on the Applications tab.
- Identity Manager Plus sends the authentication request directly to the SP since you are already logged in to Identity Manager Plus.
OAuth
OAuth is an authorization protocol that allows access to authenticated resources between servers and services without sharing credentials. OpenID Connect is an identity layer on top of the OAuth framework.
The basic components for the operation of OAuth and OpenID Connect are:
- User: This is the account you are trying to log into the client application with.
- Client Application: This application relies on the server to verify the identity of the user.
- Server: This entity validates the user’s credentials and provides the key for login. In our case, Identity Manager Plus acts as a server.
OAuth 2.0
How OAuth enables SSO:
- After successful verification of user data at the end of the application, the user logs on to the application.
- The user enters their credentials here. Upon successful verification, Identity Manager Plus sends an authorization code to the application.
- A user attempts to log into an application. The application sends an authorization request to the licensed Identity Manager Plus. The user is redirected to the Identity Manager Plus login page.
- The application now sends a request for user information along with the access token as proof of identity to Identity Manager Plus. The response to this request returns the user profile details needed to complete the sign-up process.
- The application returns the authorization code to Identity Manager Plus to get the access token and refresh token. The access token acts as a temporary key for the user to access the application’s protected resources. The refresh token is a permanent key that can be used to request a new access token after the old one expires.