More than a decade has passed since the existence of SIEM tools and these tools can be considered as an evolved example of past log management software. SIEM is a software that is a combination of Security Event Management (SEM) and Information Security Management (SIM) technology.
IT teams use SIEM technology to review event logs and data from a business’s networks, systems, or other IT environments, understand cyber threats, and prepare accordingly. Instead, they use SIEM toold to retrieve and report on log data.
In general, the implementation of SIEM provides a comprehensive approach to monitor the status of the information technology environment and operations of organizations. SIEM is a software that has many positive features; including:
- Ability to detect various threats
- Sending security alerts to relevant devices to activate incident response instructions.
- Use real-time analytics to aggregate relevant security events and create prioritized alerts.
- Receiving large volumes of data at the level of the entire organization (including the internal environment of the organization and cloud-based environments).
One of the most important features of SIEM is that it can detect various threats. In many situations, senior security operations managers fail to identify a cyber threat. In such a situation, SIEM components can be very helpful and provide the possibility to detect threats.
What are the advantages of SIEM?
In general, SIEM software helps security operations center analysts in the following areas:
- Identify threats
- Investigation of unusual activities
- The ability to fully monitor the organization’s environment
- Creating the necessary warnings for the appropriate response by SOAR tools.
What value does the best SIEM solution have for your business?
Security threats in any big or small company can cause heavy and irreparable damages to you. Time is of the essence to minimize the impact of security incidents. Studies show that, on average, it takes more than 200 days to detect an intrusion and at least 70 days to deal with it.
Surely, in this way, a company can minimize its losses by detecting and eliminating the threat in the shortest possible time. Deploying the best SIEM will help you minimize the time it takes to detect, investigate, and respond to security intrusions.
This will help you to control costs in the best way and spend your budget in the direction of more profit.
What is the meaning of detection of threats in SIEM?
The concept of SIEM can be used to identify unknown threats that require spending a lot of time to detect. As we mentioned, along with the increase in the security of organizations, hackers have been trying to penetrate these security walls. So, in this way, as a security officer, you need to be able to identify the smallest changes in the network, system and users. This recognition and identification using SIEM implementation is not a difficult task and can be done easily.
After you have identified a threat, you can use SIEM solutions for further investigation and obtain automatic data analysis methods. With this access, you no longer need to manually analyze the data. By doing this, you can spend your time reacting to new incidents and threats.
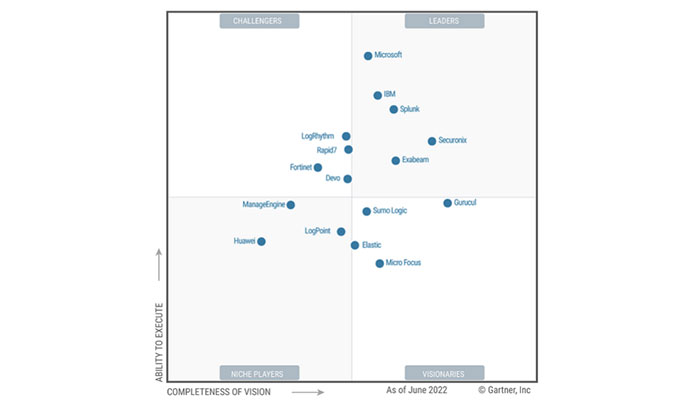
SIEM solutions
There are different solutions for using SIEM services. As you can see in the picture below, the reliable company Gartner has divided the available solutions in this field. As you can see.
According to this company, various software companies such as Microsoft, IBM, Splunk, Securonix and Exabeam are among the leading solutions in this field. In the following, we will introduce some of these pioneer solutions.
Splunk SIEM
Splunk SIEM is a security platform designed to improve the use and analysis of security-related data through big data security analytics. The goal is to provide security professionals and decision makers with tools to properly analyze threats. This product can be integrated with public, private and hybrid cloud structure as well as a service-based environment.
Splunk SIEM key features
Threats blocked
Splunk SIEM can help identify and remediate all security threats, including ransomware, encryption, DDoS attacks, malware, phishing, insider threats, and more.
Sources ingested
Splunk’s app store, Splunkbase, has more than 900 apps from various security technology organizations.
Performance
Splunk ES customers can use it for terabytes per day.
Value
Gartner customers who have implemented Splunk License are concerned about the licensing model and the overall cost of implementing the solution. However, those willing to pay the price of Splunk ES will likely see a good ROI. A large US cabinet-level department replaced a legacy SIEM tool with Splunk Enterprise, saving $900,000 per year in software maintenance.
Implementation
In the case of Splunk Cloud and Splunk ES implementation, if data sources are available, it can be done within a few days. Organizations must work with a Splunk partner that provides supported hardware integration. In general, the implementation time for any organization takes from a few days to a few weeks.
Support
Customers can choose between Standard and Premium Success Plans. The Standard plan is for businesses with typical needs, and the Premium plan is for businesses that want rapid deployment and rapid product adoption (starting at 500 GB capacity).
Scalability
Very good. There are no specific limits on servers, users, or the scale of ES usage.
IBM Security QRadar SIEM
QRadar collects and aggregates all information, reports and data from thousands of network members and applications to enable appropriate solutions to problems by analyzing the data. IBM QRadar SIEM software is available to users both as an application and software installed on computers and in the Cloud environment.
IBM SIEM key features
Adaptive management
The security team of companies and institutions can apply methods according to the organization’s internal policies and other policies to detect and track threats using the reports and templates pre-built by IBM QRadar SIEM.
Instant detection of threats
This software analyzes the network entry as well as the main and sub streams of the network to detect threats and then creates alerts with different priorities for these threats in the network.
Saving time
With IBM Security QRadar SIEM software, network monitors can observe threats in an integrated and automated manner. With this method, the monitoring and tracking that was done manually is done mechanized and with software, and network analysts can focus on problem solving and threat removal methods.
Comprehensive insight into the network
By using this software, it is possible to monitor the reports, events and happenings that exist in the context of different levels of the SaaS and IaaS network and have a comprehensive insight on them.
GoLicense offers a range of purchasable Splunk platform licenses that cater to various organizational needs, from basic monitoring to extensive data analytics capabilities.