By using two useful and licensed solarwinds software, SolarWinds IP Address Manager (IPAM) and SolarWinds User Device Tracker (UDT), you can use all the capacity of your network infrastructure by covering all the needs of your organization in the field of IP Controlling.
This combination of these licensed software from SolarWinds provides a very useful package to network managers in companies and organizations. In the following, we introduce the features of these two applications.
SolarWinds IP Address Manager (IPAM)
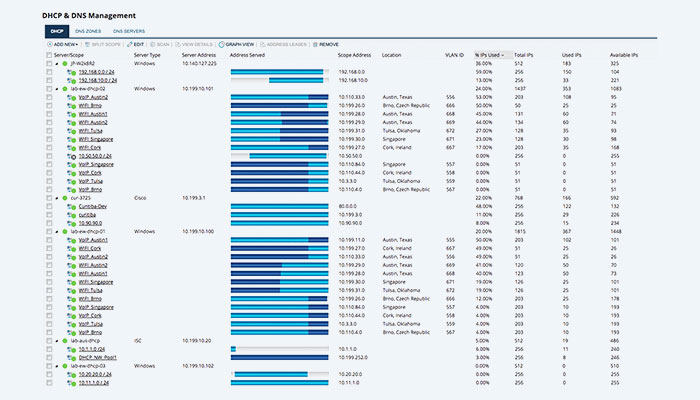
Software for managing IP addresses and other related resources in a network environment is referred to as IP management software. IP address management software is designed to help administrators manage the DNS and DHCP services, which assign and resolve IP addresses to machines, respectively.
The licensed SolarWinds IP Address Manager (IPAM) solutions can also offer extra features like the ability to manage DHCP reservations for IP addresses, data aggregation, and reporting to make the IP management process simpler. The best IPAM software will seamlessly integrate DNS and DHCP, keeping both up to date based on the IP addresses given to clients by either system.
IP addresses that are currently in use, along with the devices and users connected to them, are just a few of the data that IPAM software can track and monitor. IP management software offers vital insights into network management elements that you can use to expedite and inform troubleshooting efforts, IP address planning, and reporting by centralizing this data monitoring into a single console view.
How vital is IP address management software?
When done manually, IP address management can be challenging, time-consuming, and a waste of resources, especially in companies with a large number of network devices. Administrators who manage IP addresses manually must maintain accurate records of which devices are given which addresses, whether the addresses are static or dynamic, and whether any IP addresses have been reserved.
Most of this data can be managed in small organizations using spreadsheets if the number of connected devices stays about the same, but as businesses grow and expand, managing IP addresses becomes challenging, if not impossible.
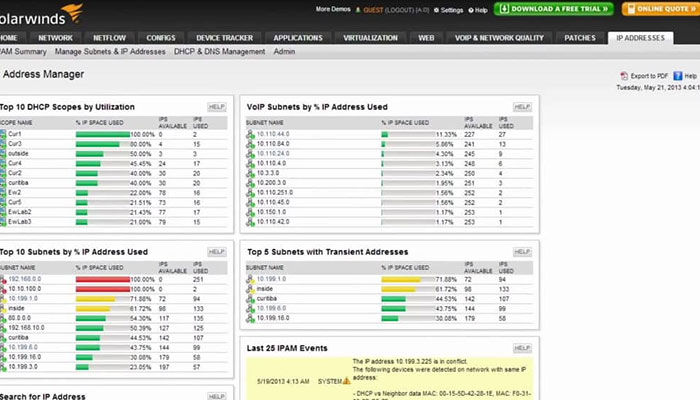
Being able to organize and track subnets with the aid of software is advantageous if you’re in charge of managing multiple subnets at once. IP management tools like the licensed SolarWinds IP Address Manager (IPAM) are crucial for troubleshooting and preventing potential network conflicts because of these factors.
For information gathering and determining the general health of a network, IP management software is helpful. IP management tools like the licensed SolarWinds IP Address Manager (IPAM) show helpful data in a centralized user console that enables administrators to see the devices connected to IP addresses and the date the addresses were assigned. By allowing administrators to quickly identify the IP addresses causing problems, IPAM solutions can be used to prevent issues like network outages.
The licensed SolarWinds IP Address Manager (IPAM) can also collect data required for legal or regulatory compliance reporting. IP management software can be used to pinpoint the origin of data breaches or other problems with knock-on effects. In order to further strengthen network security, these applications can be used in conjunction with network access control. This is because data gathered by IP management tools can show whether security software is current and functioning as intended. In addition, IPAM software can be used to spot changes in IP addresses or unusual network traffic patterns that might indicate malicious activity or security flaws.
Requirements for managing IP addresses.
There are specific features and capabilities to look for when choosing an IP management tool in order to provide effective management of the difficult and complex task of managing IP addresses.
IP address tracking is automatic
Stop using spreadsheets to track IP. IPv4 and IPv6 address management is actively possible with software.
DHCP, DNS, and IP management integration
You can find and manage subnets and the associated address blocks using active scanning. To quickly locate (and reclaim) abandoned IPs, view transient IP addresses.
Announcing, resolving issues, and reporting
You need tools that can track IP address usage and problems. Use alerts and reports to identify and resolve IP conflicts, subnet/scope exhaustion, and inconsistent DNS entries.
Support for multiple vendors
Managing DHCP and DNS servers from a single console can help you save time and prevent mistakes. Select a tool that works with the Microsoft, Cisco, BIND DNS, and ISC DHCP servers. Learning about scopes, DNS zones, and resource records is helpful.
Requests for static IP addresses on autopilot
Pick a tool that enables quick static IP address reservations. Depending on your needs, you can also track IP requests for compliance or change management.
Support for APIs
You can look for API support that provides “Create, Read, Update, Delete” (CRUD) operations and integration with external software. The management of DNS or IP records may be automated with the aid of this feature.
Blending of virtual environments
In order to automate IP address provisioning and update DNS records on virtual machines, look for IP address management that extends to VMware environments.
DNS cloud monitoring
You can centralize the monitoring of AWS and Azure zones and records by using an IP management tool.
SolarWinds User Device Tracker (UDT)
User Device Tracker (UDT) is a tool created to assist you in managing network access requirements and risks related to the proliferation of IP devices. You can maintain control over who and what connects to your network with UDT’s automated user and device tracking and strong switch port management capabilities. With a quick search on a username, IP address, hostname, or MAC address, you can locate a computer or user and find misplaced or rogue devices.
Maintaining a list of switch ports that are free and those that are in use is one of the biggest problems that network administrators encounter. The planning of new network requirements, ensuring optimum port usage, and meeting compliance requirements all greatly rely on this information. Switch ports that aren’t in use can be exploited by hackers to access the network, which is another security risk. When done manually, maintaining switch port utilization information is laborious. The number of devices increases along with the network, making it more time- and effort-intensive to maintain an accurate inventory of device data.
SolarWinds User Device Tracker (UDT) Key Features
The operation of switch port mapping
In a database known as the Management Information Base (MIB), device information like port details are kept. While polling the network for device information, network device tracking software like SolarWinds User Device Tracker retrieves specific port data from devices like switches and routers. This data is very helpful for capacity planning and troubleshooting to identify a problematic device on the network by visualizing switch port utilization and status.
Switch port monitoring
All switches can have switch port monitoring enabled if administrators require information on port utilization, CPU load, memory usage, and detailed port data in addition to current and historical port utilization information. Every device is automatically found and checked for user or port information.
Advantages of switch port monitoring.
The switch port monitor’s ability to automatically identify switches that are operating at or close to capacity is its most significant advantage. Unused ports can be quickly reclaimed, enabling wise capacity planning and purchase choices. Switch port monitoring offers information on network switches by active ports, CPU load, memory usage, etc. To find out about current and past port utilization, you can even delve deeper into a given port’s data. These reports are crucial for fulfilling compliance requirements.
Accurate information on unused switch ports aids the administrator in keeping these ports closed, which is a best practice for protecting your network from security risks.
Switch port management and device tracking automation
- Allows for whitelisting, watch lists, automatic alerts, and clickable port shutdown.
- Switches, ports, and network devices are automatically found, mapped, and monitored.
- Gives comprehensive switch port usage information, capacity analysis, and built-in reporting.
- Allows you to track endpoints by searching on their MAC address, IP address, username, or hostname.
- Identifies devices quickly and retrieves user name, port information, connection history, and other information.
Software for tracking network devices in action
The primary function of comprehensive network device tracking software, despite its many features, is to find users and devices on the network. Using discovery features, this is frequently accomplished. The licensed SolarWinds IP Address Manager (IPAM) can start adding ports once it has found and added devices using device discovery technology. The two-step procedure ensures that IT administrators are ready to go right away.
Discovering a user or computer. It may be simpler to quickly locate a specific endpoint device on LAN and wireless networks if all of this network data were collected and stored in a single location. All you have to do is perform a search using an IP address, username, hostname, or MAC address. Once the device has been located, a single device tracking console can instantly provide switch name, port, port description, VLAN, VRF, and vendor information.
IT administrators can be notified when unknown devices enter a network by using network device tracking software. You must first provide a device whitelist in order for this to occur. All gadgets considered “safe” are listed on the whitelist. Devices that aren’t on this list are referred to as “rogue. As soon as these malicious devices join the network, you’ll get a notification.