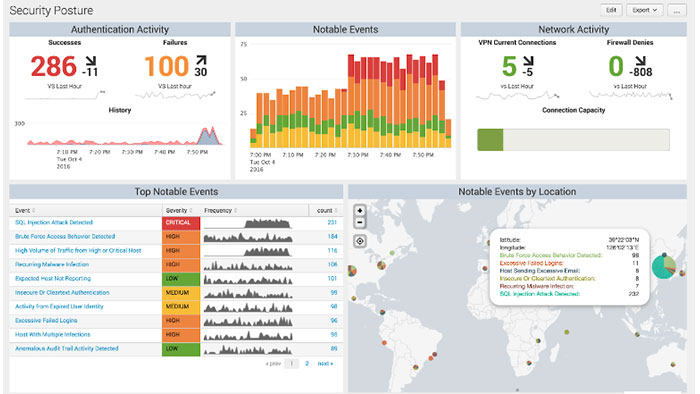
Application Performance Monitoring
The second, third and seventh layers of the network are the most common layers used for network monitoring. Application Performance Monitoring use these layers to discover devices on the network and how they are connected, generate network topology maps, and monitor the network using software such as Splunk License.
Before addressing the issue of network monitoring, it is best to know the common devices on the network. These devices are as follows:
Switches
Switches can computers, servers and other devices to a private network. Switches, as a controller, are able to communicate with each other on theconnect network. Switches are second layer devices.
Application Performance Monitoring
Routers
Routers connect networks to each other. A router acts as a distributor. In such a way that it can choose the best way to exchange information. Routers connect users to the Internet. It should be noted that routers are third layer devices.
Servers
These are the networks that deliver applications and information to the users of an organization. The reason for this is that programs and information are placed directly on the servers and their retrieval is done directly from the servers. The server receives user requests and responds accordingly.
For example, when accessing a website from anywhere in the world, a web server, regardless of your location, provides web pages to your local device. There are other examples of servers, such as email servers and database servers.
Firewalls
Firewalls are responsible for protecting networks against internal and external threats. The firewall controls incoming and outgoing traffic according to the rules set by network administrators. A firewall creates a secure barrier between a trusted private network and an unreliable network such as the Internet.
How does data pass through the network?
Private networks connect to the Internet using routers. Information is sent over the Internet in the form of data packets. Each data packet contains a destination IP address that routers use to send information from one location to another. When a router receives a data packet from the Internet, it transmits it to the private network.
On most networks, data packets must first pass through a firewall. The purpose of this is to keep the private network secure. The firewall does this by filtering traffic between the Internet and the private network.
Why is network performance monitoring important?
The network is the life line of the IT infrastructure. When networks fail, the flow of information required by programs and business operations stops. Networks are a dynamic environment. Therefore, network admins are constantly asked to add new users, technologies and applications to their networks. These changes can affect their ability to deliver consistent and predictable network performance. When certain problems occur on the network, the network administrator is pressured to determine the root cause of the problem before it affects users, applications, and businesses.
Solving this problem with intermittent performance problems that are difficult to repeat and diagnose is even more problematic. Many IT organizations are referred to as Service Level Agreements (SLAs). SLA commitments are often included in IT compensation programs. SLAs are performance guarantees that are measured and reported.
Principles of network performance monitoring systems
Network monitoring systems such as Splunk offer five main functions:
Discovery
To set up network monitoring, you must first find the devices on the network. In fact, network monitoring begins with the discovery process. Keep that in mind, if you do not know what is in the network and how they are all connected in the network, you can not monitor that network. Network monitoring systems detect devices on the network, such as routers, switches, firewalls, servers, printers, and more. You can easily do this by using Splunk software and its licenses.
Map
To monitor the network, it is better to visualize your network. Network monitoring systems create network maps. Network maps are a powerful first response tool that enable network administrators to visualize their networks. They represent clean and tidy parts of the wiring in the network. Many NMSs require a significant amount of manual processing to create a network map. Some of them are just a tool for drawing the network and also trust the knowledge of the manager network.
Monitor
Using network management software such as Splunk, network administrators can change the role of devices or create new ones from scratch. Network monitoring systems expose the network administrator to large choices.
Alert
Network monitoring systems, such as Splunk, automatically notify the network administrator when a network problem occurs. These applications can send alerts via email, and text message. Threshold-based alerts enable network administrators to respond to problems before they affect users, applications, or businesses. For example, network monitoring systems are configured when more than 80% of the processor is used. This allows the network administrator to handle and react before the router is completely broken.
Report
Network administrators are primarily involved in the design, analysis, and redesign of the network life cycle. To support life cycle, network monitoring systems provide real-time monitoring data.
How does Application Performance Monitoring work?
Monitoring systems such as Splunk monitor networks, devices, and network servers to find performance data using standard protocols such as the following.
- WMI or Windows Machine Interface
- SSH or Secure Shell for Unix and Linux Server
- SNMP, Simple Network Management Protocol
Some network monitoring systems support scripting languages, such as Powershell, to create custom monitors for Windows servers. They can be used to create custom monitoring for specific organizations’ databases. Currently, the two most widely used monitoring protocols are SNMP and WMI. They provide network administrators with thousands of different monitoring methods to assess the health of networks and their devices.
GoLicense offers a range of purchasable Splunk platform licenses that cater to various organizational needs, from basic monitoring to extensive data analytics capabilities.