Nessus (Tenable license) is a system vulnerability scanner program that can look for, find, and report different kinds of vulnerabilities on any gadget. Tenable Network Security is the company that created and supports this vulnerability scanner. Purchasing a license will give organizations and businesses better access to this software. In the shortest amount of time, this vulnerability scanner can reliably and accurately identify a variety of vulnerabilities. Currently, one of the most well-liked and sophisticated vulnerability scanners available is called Nessus Security.
Why Tenable?
Most network security testing tools are extremely advanced in terms of network security. Software like Nessus Security (Tenable license) will undoubtedly make the process simpler. With just a click of a button, this software can quickly give you a customized network security report and is very simple to use.
The first step in any attempt to hack the local network you have established for your business or organization is a vulnerability scan, followed by a penetration test. Look for any potential gaps by scanning the openness of various devices and network nodes.

Open ports, outdated software with known security flaws, or default passwords on devices are just a few examples of these potential network danger points. A hacker searches for weaknesses, tests them, and then devises a strategy to take advantage of them. There are two steps to finding these vulnerabilities. A penetration test verifies that this can actually be exploited because the scan only flags potential issues.
Nessus Security is a piece of commercial software that comes in both a free and a paid version. You must purchase the necessary licenses (Tenable license) in order to obtain the paid version. Although the free home version of this software also includes many tools to help you find and fortify your network, it is typically designed to look for vulnerabilities. The commercial version of the software has no restrictions on the quantity of connected IPs or vulnerabilities found, and the software license can be easily moved to another system if necessary. This version also makes it very simple to report evaluation results, and reports can be sent via email.
Nessus software makes it simple for IT managers and security managers to find and fix vulnerabilities, bugs, malware, uninstalled security patches, and configuration issues in organizations and businesses. Nessus Management Dashboard has a very user-friendly interface, a number of templates for predefined scenarios that can be customized, and this software also enables quick and effective system and network scanning. This software scans the network for various vulnerabilities with the aid of its strong plugins.
Top vulnerability scanner Nessus
The following characteristics of Nessus Security (Tenable license) make it superior to other software currently on the market.
The leading vulnerability scanner, Nessus
The following features can be mentioned as reasons why this software is superior to other programs currently on the market:
Reliability
In addition to being used by 30,000 public and private organizations globally, Nessus Security Scanner has received over two million downloads.
Extreme precision
In comparison to other vulnerability scanners, Nessus Security Vulnerability Scanner has the fewest false positive errors in the results of vulnerability assessments with a 99.99 percent detection accuracy.
Proper vulnerability protection
This scanner has the highest detection rate for software and network vulnerabilities among comparable products, with more than 60,000 CVEs found. Within 24 hours of the disclosure of the vulnerabilities, Nessus add-ons will also be accessible to owners.
Ready-made patterns
Nessus Security Scanner has over 700 pre-configured vulnerability assessment models that are compliant with international standards like CIS, DISA, STIG, HIPAA, PCI, DSS, USGCB, FDCC, etc. … has one of the best performances in this regard . These pre-configured patterns cover a broad range of hardware and software tools and aid in quickly pinpointing the precise location of the vulnerabilities from the time the vulnerabilities are assessed until the point at which they are fixed.
A sophisticated reporting system that allows for customization
In accordance with the type of vulnerability, host, plugin, etc., Nessus Security Scanner enables you to receive multiple reports. These types of reports can be easily generated thanks to its user-friendly interface. After each scan, these reports can be automatically sent via email in the following formats: HTML, CSV, PDF, Nessus XML, and Nessus DB.
Vulnerabilities in groups
It is simple to recognize and prioritize vulnerabilities thanks to vulnerability classification based on critical degree. This shortens the time needed to fix these points and keeps malicious attacks from getting inside. The vulnerability handling procedure may also be delayed for a predetermined amount of time. You can concentrate solely on vulnerabilities with the aid of these features and fix them.
Live outcomes
In accordance with the history of the scans conducted and the new plugins installed, Nessus Security Vulnerability Scanner determines your vulnerabilities automatically after each update of the plugins, ordering, and licensing. It then displays those vulnerabilities to you. So you can quickly find new vulnerabilities and fix them.
Installation on the majority of platforms
Nessus (Tenable license) software can be installed and used on a variety of Linux distributions, Windows operating systems, and Mac OS.
The NESSUS scanner has a competitive edge over competing products
When selecting a vulnerability scanner, this software’s advantages over its rivals can be very important.
Usage simplicity
You can create the policy you want and use it to scan all network assets with just a few mouse clicks.
High degree of vulnerability detection accuracy
Finding vulnerabilities is done quickly by Nessus Security Vulnerability Scanner. Additionally, this program displays the fewest false positives.
Broad spectrum of identification
The Nessus Security Scanner has the most vulnerabilities identified among its rivals, with over 60,000 known vulnerabilities.
Strong plugins
The detection and detection abilities of this well-known security scanner are improved by Nessus-specific vulnerability scanner plug-ins, which Tenable security researchers are constantly updating.
Affordable
This product meets all requirements for a vulnerability scanner, has the broadest coverage of assets, and eliminates the need for you to buy additional products in this area.
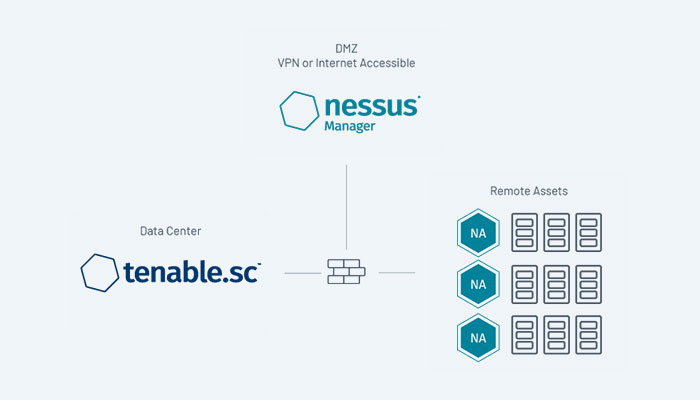
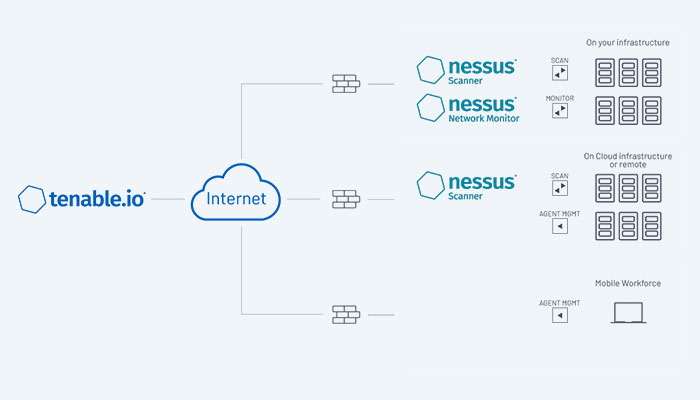
Tenable Architectures in networks
The Tenable platform depends on a number of Windows services that are housed on virtual machines (VMs). This infrastructure must be supported by your environment. Directory Listeners, Security Engine Nodes, and Storage Managers are the three parts of the Tenable.ad platform.
- The Directory Listeners receive real-time Active Directory flows and employ a number of treatments to decode, isolate, and correlate security changes while closely collaborating with the monitored domain controllers.
- The Security Engine Nodes: The Security Engine Nodes host analysis-related services and provide end-user applications (like the Web portal, REST API, or alert notifier) as well as support for the internal communication bus and Tenable.ad security engine. This part is based on various isolated Windows services.
- The Storage Managers: In addition to managing data delivery to the Security Engine Nodes and Directory Listeners, the Storage Managers support hot and cold storage. Only this element needs to be persistent in order to save data. To store internal data and configuration, they use Microsoft MS SQL Server internally.
The on-premises solution from Tenable.ad is based on one of the following architectures and uses a software package hosted in a specific Windows Server environment that you supply and manage.
OpenCentralized Architecture
All Tenable components are housed in one network zone by the centralized architecture.
- The three key parts—Directory Listeners, Security Engine Nodes, and Storage Managers—operate in tandem and are able to communicate with one another without the use of network filtering.
- Tenable advises that you secure this architecture with a firewall at the zone’s entrance to ensure proper network security. The incoming and outgoing network flows are depicted in the following diagram according to the Network Flow Matrix.
Advantages
This architecture provides the best manageability and security compromise.
- Each Tenable.ad service is located at the same physical location and is protected by a different firewall.
- Each service flow (Active Directory, end users, alerts, etc. ) passes through the same network hardware.
- Because it doesn’t require any additional configuration or services on the targeted domains, this architecture links new Active Directory domains quickly.
Disadvantages
Having to transfer every Active Directory flow from the monitored domain controllers to the Tenable.ad network zones can cause the centralized architecture to use up bandwidth.
Distributed Architecture
As shown in the following illustration, the distributed architecture hosts the Security Engine Node and the Storage Manager in one network zone while placing Directory Listeners in the same network zone as the domain controllers.
Advantages
- Reduced bandwidth: Active Directory flows can be substantial when tracking large directories. The Directory Listeners decrease the platform’s bandwidth usage by filtering pertinent security changes and compressing the objects.
- better network filtering
- Numerous TCP and UDP ports used by an Active Directory infrastructure can be targets of a cyberattack. Tenable advises that you expose these network ports only when absolutely necessary, adhering to the principle of least privilege.
- Tenable.ad eliminates the requirement to expose Active Directory ports to a different network zone by putting Directory Listeners in the same network zone as the domain controllers.
- Infrastructure that is totally isolated from the rest of the information system is sometimes necessary due to particular circumstances. Tenable.ad’s platform only needs one inbound and one outbound network flow thanks to the distributed architecture, which protects the security of the isolated infrastructure.
- Security on the network: Tenable.ads’ Directory Listeners employ a particular host-based firewall. The Security Engine Nodes and Storage Managers are located in a zone, and Tenable advises using a specific firewall at the zone’s entrance.
Disadvantages
The only environments for which Tenable advises using this architecture are those that demand the highest level of network isolation.
- Given that it necessitates multiple network configurations in various network locations, the distributed architecture is more difficult to deploy and maintain.
- This architecture is also less adaptable because it necessitates the deployment of new Directory Listeners each time the customer wants to add a new domain to monitor.

