Cisco ISE License Types
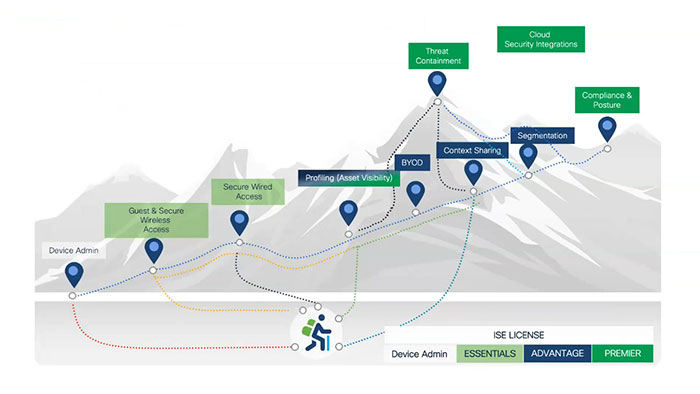
You will need the appropriate Cisco ISE licenses to use certain features, as the following image briefly illustrates which licenses you will need for ISE use cases.
For example, if you are looking for guest network security such as digital wired or wireless access, you simply need Cisco ISE licenses. If you want to manage your mobile device according to your compliance, you need Cisco ISE premium licenses.
Please note that the paths in the picture don’t cover all the customer journeys and each customer can have their own customer customized ISE journey. Some customers start with guest access, some customers can start with BYOD feature, for some customers threat containment or posture can be the first step. There is no right or wrong in designing your own ISE journey.
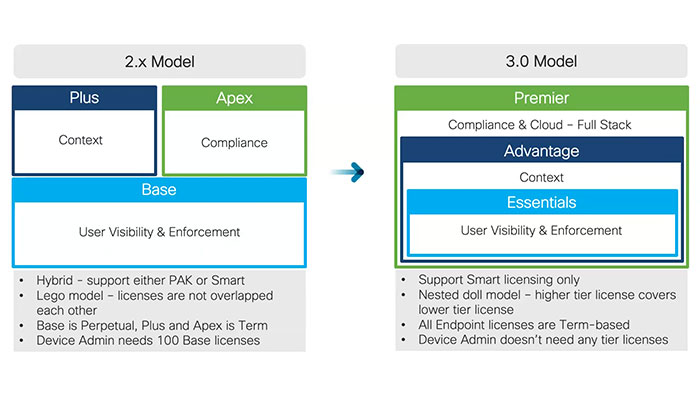
Essentially, the Cisco ISE licensing structure used in ISE version 2.x release is called the Lego model. There are three different license tiers: Base for user visibility and enforcement, Plus for context and Apex for compliance. It is called the Lego model because you can assemble your licenses as you need their associated features. The features you can use with one license, don’t overlap with the features you can use with another license and you have to have Base license to use Plus and or Apex license.
The most significant change in Cisco ISE 3 is the hierarchy of the license tiers which called the nested doll model. In this model the higher tier license covers the lower tier license. So you can use any ISE features with essential license if you have advantage or premium license. Also, you can use any ISE features with advantage license if you have premier license.
The new licensing structure is much simpler than the 2.x licensing model. For example, to fully use Cisco ISE functionality in ISE version 2.x you need three different licenses. But you need only one license in 3.0 model. Another significant change is that Cisco ISE 3 licenses support only smart licensing. when a smart license token is active and registered in the Cisco ISE administration portal, the Cisco smart software manager or CSSM monitors the license consumption by each endpoint session or product license. So you need your smart account registered in the CSSM and your ISE deployment needs to be continuously connected to the CSSM to monitor the license consumption.
However, in case that customers are not willing to connect their devices to the Internet and any inbound or outbound connection would violate their network security policies, they can use Cisco ISE PLR license or Cisco ISE permanent license reservation which enables all premier capabilities on the product permanently. This license also includes device admin license and Cisco ISE virtual license.
Moreover, all tier licenses including the essentials license are now time based why the device admin license is still perpetual. Additionally, device admin licenses no longer need any tier licenses in 3.0 whereas it needs at least 100 base licenses in 2.x model.
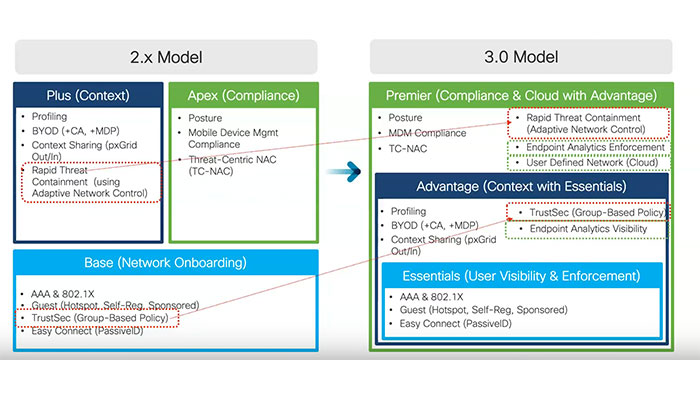
In general, the Essentials license equals to the Base license, Advantage license is equivalent to Base and Plus licenses, and Premium license is identical to Base, Plus and Apex licenses.
Now let’s look at the changes. First, group based policy (TrustSec) for trusted customers requires advantage license in 3.0 while it needs base license in 2.x. This change makes ISE licensing structure more aligned with Cisco DNA center licenses since you need advantage license for segmentation in DNA center. Also even in ISE 2.x, it was encouraged to have Plus license to fully use TrustSec attributes. So it wouldn’t be a significant change practically. Second you need Premium license for rapid threat containment or RTC using adaptive network control or ANC. This change provides more consistency as you need Premium license for threat relevant features. There are new features available in ISE 3.0. you can use AI endpoint analytics visibility with Advantage licenses and enforcement with Premier license. Also with Premier license you can use user-defined network or UDN which is a Cisco network solution providing secure and remote onboarding of client devices. It also allows IT staff to give each user oversight of their own network partition.
Benefits of Cisco ISE New Licensing model
The new licensing model brings the consistent licensing structure with Essentials, Advantage and Premier that being used across Cisco. Also, the nested doll model provides more simplified solution. As higher tier license covers lower tier license, you don’t have to have multiple licenses for one active endpoint session and you don’t need to consider other license tiers when you estimate how many licenses you would need. After that, basic support is included in all the key licenses. You need to purchase separate service skills only when you need enhanced or premium support. Of course ISE 3.0 now supports only smart licensing, so if you have a smart account for other Cisco products you can easily leverage your experience to manage your ISE licenses in your smart account.
Cisco ISE License Consumption
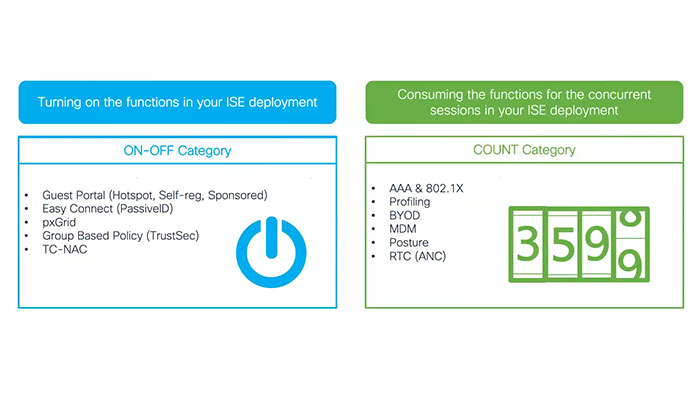
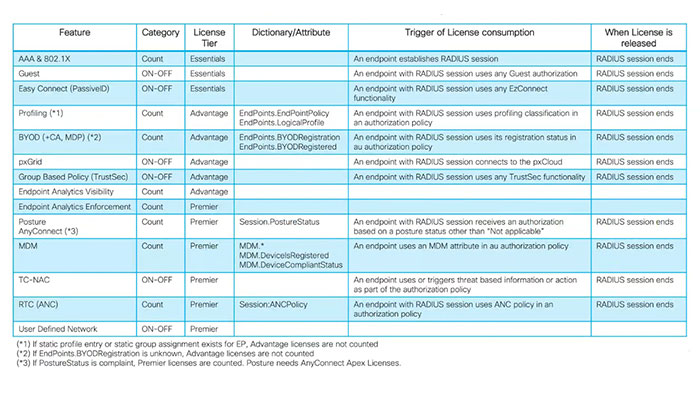
Cisco ISE features can be divided into two different groups based on how they consume licenses.
First, there are features that need a license to turn on the function in the ISE deployment. Guest service, easy connect, context sharing or pxGrid, group-based policy and threat centric NAC are included in this ON-OFF category.
Features in another group consumes as many licenses as the number of the active concurrent sessions in your ISE deployment such as AAA and 802.1X, profiling BYOD, MDM, posture and RTC are included into this category. The following table summarized how each feature consumes licenses:
Generally, to avoid the situation that your ISE deployment is consuming more licenses than those are entitled to you, it is recommended that you register more licenses than the number of endpoints in your network these are.
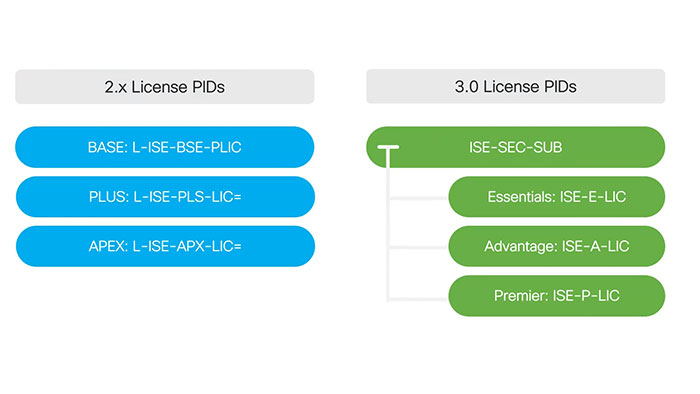
Cisco ISE License PIDs
You can find the Cisco ISE license PIDs in the following figure: