Best SOAR Tools and Solutions
SOAR stands for Security Orchestration, Automation and Response in the field of cyber security. SOAR helps organizations and small or large companies to be able to collect data related to security threats from various sources and react appropriately to low-level security threats without the need for human intervention.
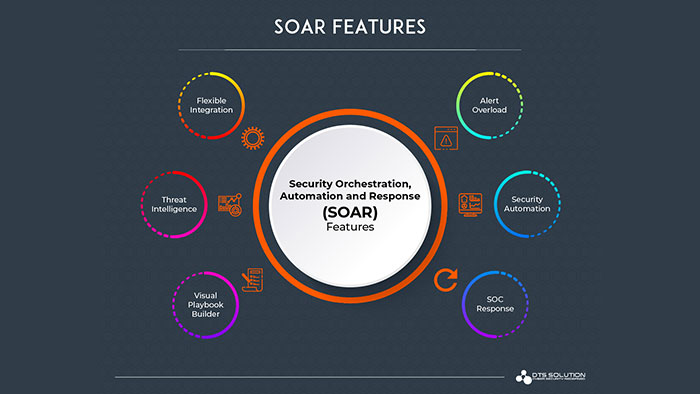
What is the purpose of SOAR?
The five main advantages of SOAR can be stated as follows:
- flexibility
- Cooperation
- Fighting budget constraints
- Effective incident management
- Improve time management and productivity
Each of these benefits is one way to address the issue of IT security. The purpose of using SOAR is to implement information security in an optimal way. In fact, SOAR combines technical and software capabilities with a system’s internal processes to improve the management of security alerts in an organization.
It can be said as follows:
Security orchestration
This automation is responsible for integrating various security tools and operating systems to automatically respond to the incident.
Security automation
This automation is responsible for performing many tasks that are important in cyber security and does not involve humans. In other words, it performs effective incident response processes by automating manual and time-consuming tasks.
Incident response
Refers to the processes that organizations use to create and correct security alerts. These incident response processes may be fully automated, manual, or a combination of both, reflecting the unique business processes of an organization.
When your security team integrates with SOAR technology, it improves security operations (SecOps) to solve MTTR and defend your organization against a variety of security threats.
Benefits of implementing security automation using SOAR
Increase efficiency
Using a robust SOAR solution, analysts can generate standard daily, weekly, monthly, or annual reports instead of spending valuable time collecting and sorting data through metrics and reports.
This includes all activities (even undocumented activities). In addition, these reports will be transparent and comprehensible and viewable against other important business metrics in terms of security. These programs keep real-time reports in centralized company dashboards so you can access them whenever you want.
Proactive removal of security warnings
Once the alerts and data related to system speed are evaluated, the bandwidth analysts examine to gather evidence and fields related to the preemptive security event. This leads to faster decision-making, which is why possible defects can be prevented.
Enhance incident response
By combining all current security tools into a unified platform that automatically detects and fixes emerging issues in real-time, you can optimize your information workflow with threat intelligence. This system allows you to react faster and smarter to all kinds of threats and to prevent possible breaches.
Powerful orchestration with automation
Orchestration allows you to improve security processes by making different resources work together. Also, move beyond reactive models and take the lead in defending your organization against threats by implementing advanced defense strategies combined with comprehensive intelligence gathering, user standardization, and job analytics.
There is many software related to the use of SOAR solutions, which can include: Splunk Phantom, IBM Resilient, DFLabs IncMan, Insight Connect, RespondX, Exabeam, ServiceNow, and SIRP. In the following we will talk more about the Splunk Phantom solution.
Splunk Phantom, a reliable SOAR solution
Cyber security teams in organizations are always working hard to detect, analyze and counter threats and face high work pressure. However, these teams are not independent in many organizations and have other duties as well, and the lack of manpower in this area is noticeable, and most organizations do not have enough manpower to analyze and deal with the high volume of security incidents.
Therefore, organizations are looking for more productivity from existing resources and increasing the efficiency of their cyber security teams and tools.
Access to expert experts to be employed in the first tier of security operation centers is very limited. It is interesting to know that more than 1 million people are estimated to lack the need for specialized human resources in the world for this field. Due to this issue, the average time to detect, handle and respond to threats is very high and this process takes place slowly.
With the help of the Splunk Phantom system, you can reduce the workload of the SOC team and automate many repetitive operations. Therefore, the SOC team is only responsible for dealing with new threats or confirming and tracking some of the most important repeated threats.
Phantom assists and empowers the SOC team by automating, tuning and rapidly responding to threats. With the help of Phantom, the SOC team can do smarter work instead of tedious work.
Automating repetitive tasks will lead to faster handling of security incidents with automatic detection, adjustment and response. Increased productivity, efficiency and accuracy will be other benefits of automation with the help of Splunk Phantom. Another benefit of using Splunk Phantom is to strengthen the power of cyber defense by connecting and coordinating complex workflows between different tools and operational teams in the organization.
With the help of Splunk Phantom, security teams can automate many tasks and define complex workflows. In this regard, following the occurrence of an incident, the relevant action is automatically implemented and various security tools available in the organization are used. Therefore, the appropriate response to each attack is given quickly automatically or with the approval of analysts.
In addition to orchestration and workflow automation, with the help of Splunk Phantom, the process of handling incidents, cooperation and coordination between experts of different levels of SOC teams can also be done.
Automation in the security operations center
The Splunk Phantom product enables security operations center analyst teams to work smarter and quickly execute required actions to automatically perform tasks that used to take hours in less than a few seconds. Security operation center teams can implement the required work cycle in playbook format visually or with the help of Python programming interface. By outsourcing these tasks to Splunk Phantom, the analyst team can focus on other critical missions.
Orchestration
Splunk Phantom is an interface tool that connects the tools and security experts located in the organization. By connecting and coordinating complex workflows between SOC teams and security tools, it is ensured that each of these components has performed its role correctly in detecting, analyzing and responding to security threats. The operations and tasks to be performed in a workflow are placed in a completely abstract form in the corresponding playbook, and the analyst will not be involved in the details of how to connect and perform various operations related to each tool.
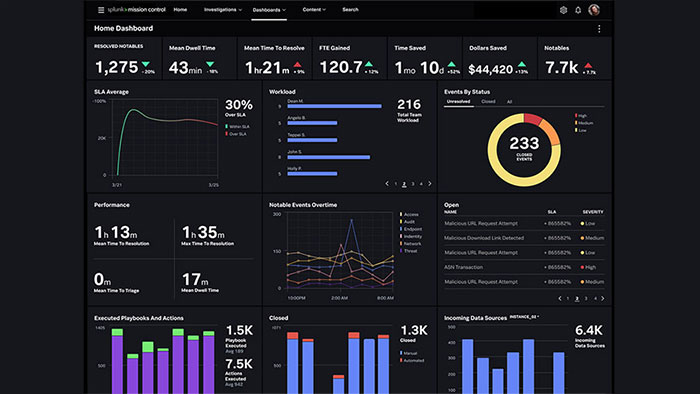
Response to the incident
Splunk Phantom helps security teams analyze and respond faster to threats detected in SIEM or other security tools. Splunk Phantom’s automated detection, investigation, and response capabilities enable security teams to automate and rapidly respond to incidents.
Even with the help of the mobile version of Splunk Phantom, analysts can monitor and intervene in the incident response workflow. Splunk Phantom’s event management capability also facilitates security operations center processes. All data and events related to each event can be tracked and viewed through the Splunk Phantom user interface. With the help of this tool, it is also possible to cooperate and exchange opinions with other members of the analysis team in the investigation of an incident.
Best SOAR Tools and Solutions

