Best WAF Solutions
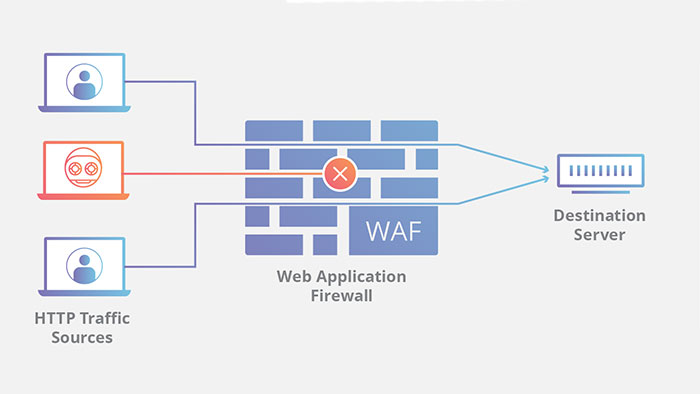
A web application firewall (WAF) protects web applications by monitoring HTTP traffic between a web application and the Internet. WAF usually protects web applications against attacks such as cross-site spoofing, cross-site scripting, XSS, file inclusion and SQL injection, etc.
WAF is a protocol layer 7 defense (in the OSI model) and typically organizations store much of their sensitive data in a back-end database that can be accessed by web applications. Also, companies use mobile applications and the internet to facilitate their business interactions. Most of their online transactions happen at the application layer. According to the OSI model, network layer seven is the layer that the user can see and interact with the application.
On the other hand, attackers often target applications to access customers’ banking information. This is where app owners need a WAF to protect their users’ data. So WAF plays an important role in cyber security.
WAF security models
WAF follows defined rules known as policies in data analysis. With the help of these policies, the firewall filters malicious traffic. These policies are constantly updated to respond to different forms of cyber-attacks. In the WAF security model, there is a blacklist and a whitelist:
Blacklist WAF
They are built based on the negative security model and resist known attacks. In fact, the firewall detects these attacks and blocks them.
Whitelist WAF
These WAFs follow the positive security model and only pass pre-authenticated traffic. In practice, many WAFs follow a mixed blacklist and whitelist approach for optimal security performance.
What threats does WAF protect the network against?
Cross-site Request Forgery
These cyber-attacks may affect all websites and web applications. Especially programs that require user login to perform a specific action. They cause the user’s browser to send HTTP requests to the website to perform unwanted actions.
Cross-Site Scripting (XSS)
Most of the time, cross-site scripting is a form of user-directed code injection attack. Hackers inject malicious code when loading web pages. Interactive websites and applications are especially vulnerable to these scripts.
SQL injection
In an SQL code injection attack, cybercriminals use the SQL query field to transmit additional malicious information.
What are the benefits of using WAF?
Companies that use a Web Application Firewall (WAF) on their website enjoy the following benefits:
Protection of legacy systems and applications
Security vulnerabilities persist longer in software that is used for a long time or that is not programmed in-house. WAF service provides more security for these systems and applications.
Reducing security vulnerabilities in multiple applications
Webmasters can deploy WAF in front of multiple applications simultaneously. This approach provides the possibility of reducing existing vulnerabilities.
Additional level of security
In combination with other security measures, WAF provides an additional level of protection against unauthorized access.
Best WAF solution for networks
Different software can be used to take advantage of WAF solutions. Software such as Akamai, Cloudflare, Imperva, Radware, Fastly, Amazon Web Services, etc.
But which one of them is a better solution for your organization? In the following we will introduce some of the best WAF solutions.
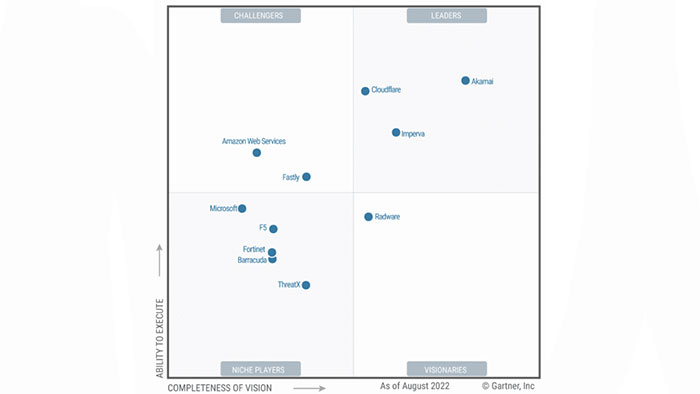
In its latest rating, Gartner Institute reviewed active solutions in the WAF field and assigned a score to each one. In the picture below, you can see the position of each solution according to the scoring based on “Ability to Execute ” and “Completeness of Vision”.
As you can see, Akamai, Cloudflare and Impreva are categorized as Leaders of this field. (Gartner WAF Quadrant 2022).
Akamai Solution
The Akamai Kona Site Defender online application firewall includes DDoS protection. DDoS services use a scale system from 1 to 10 to identify and remove threats from IP addresses. These ratings determine how well an IP address can detect suspicious activity. Privileges are used to allow, notify or block based on the severity of the privilege. Additionally, users may change settings to specify which IP addresses should be blacklisted.
The web application firewall checks each part of the traffic separately. They stop any violent attacks. This program deals exclusively with attacks launched through the web. Users may obtain data such as reports and attack rates through the admin dashboard. Minimal optimization is essential for performance.
In a cloud solution called Site Defender, Akamai, the world leader in DDoS mitigation, integrates complete DDoS protection with its web application firewall. A significant advantage of integrating these services into one security package is that you are not routing your traffic through two separate organizations to get valid requests to your web server.
Akamai is often the first to discover new exploits because it is a leading Internet security software provider. As a Site Defender user, you immediately benefit from this “ahead of the curve” knowledge with more accurate and intelligent bans on hacker traffic.
Cloudflare WAF
A company called CloudFlare provides distributed domain name server providers, DDoS mitigation, Internet security, and content delivery services. They will protect all online property. CloudFlare protection is always on, thanks to continuous upgrades.
Cloudflare handles a huge volume of requests every hour while simultaneously detecting and blocking new threats. The platform may rely on crowd intelligence to eliminate risks due to its large user base. In other words, Cloudflare chooses whether a new WAF rule created by a customer applies to all other domains in its network.
Imperva WAF
A cloud-based web application firewall is also available from Imperva (WAF). It offers application delivery with content caching, load balancing, advanced bot protection, API security, web application security and DDoS mitigation across a worldwide content delivery network.
All incoming traffic to your online services passes through Imperva’s web application firewall. Blocks malicious users and requests including XSS and SQL injection. To protect its users, Imperva uses network-based attack intelligence. Imperva WAF maintains monitoring thanks to 24 DDoS scrubbing data centers around the world.
Other web augmentation services, such as a content delivery network (CDN), work with the Imperva Cloud WAF service, which speeds up the flow of web pages and ensures constant availability if the main server goes down for maintenance or is damaged. The WAF has a virtual patching service that updates the protected system with all necessary patches and maintains access to the site while the web server is being restored.
Imperva offers a managed services option for its Cloud WAF that includes experts and technicians to manage the security program. Imperva WAF Gateway offers a variety of network equipment a version of the Imperva Security Service.