Cisco SDWAN Edge Platforms
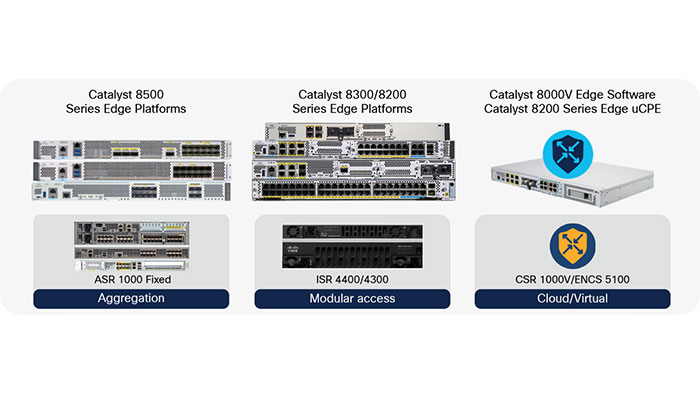
Lately, Cisco Catalyst 8000 is announced as a new Cisco SDWAN edge platform which can drives many new features and delivers SD-WAN success. These new flexible edge platforms support SD-WAN and cloud networking use cases and there are three major platforms within the Catalyst 8000 family:
The Cisco Catalyst 8500 is designed to replace the ASR 1001-HX / ASR 1002-HX and is positioned at the data center/colocation for extremely high performance.
The Cisco Catalyst 8300 is designed to replace the ISR4400 and is positioned at the branch. This innovative platform offers very good performance but also focuses on delivering services like switching, VoIP, security and more at the branch in a compact footprint.
The Cisco Catalyst 8000v is positioned to replace the CSR100v. This one is designed to run in virtual environments and on cloud marketplaces such as VMWare ESXi and Amazon AWS.
Cisco SD-WAN Deployment
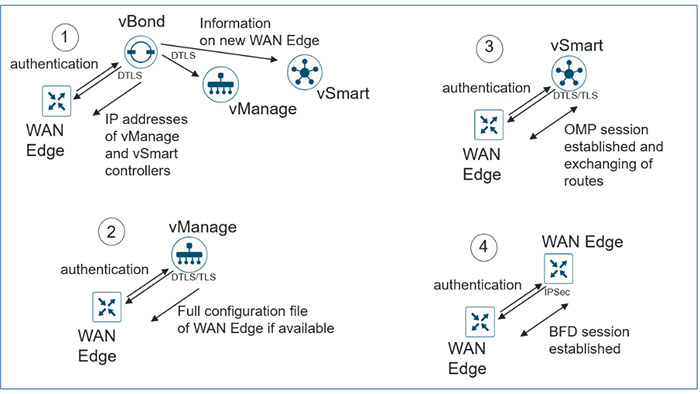
The SD-WAN controllers and vEdge platforms need to mutually authenticate and trust each
other before establishing the secure control connections. As soon as, the SD-WAN controllers authenticate each other and WAN Edge devices, they will validate the root of trust for the certificate root CA, compare the organization name and check the certificate serial number authority. You can find the SD WAN onboarding steps in the following figure:
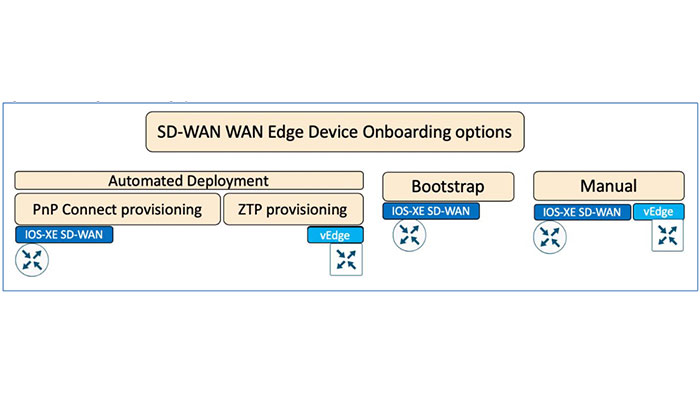
There are several options available to securely onboard SD-WAN Edge devices. Generally, customers should use the PnP provisioning for their IOS-XE-based devices (cEdge) and ZTP for Viptela Edge (vEdge) devices. Also, Bootstrap config is only supported on the IOS-XE SD-WAN.
Cisco Plug and Play Process
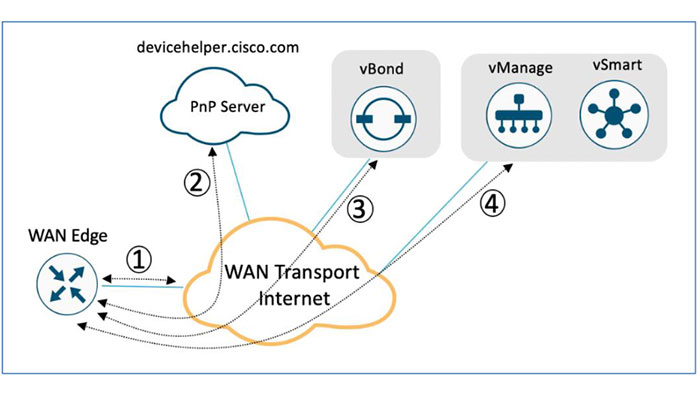
The cEdge device on boot up, obtains IP address, default gateway and DNS information via DHCP on the PnP interface that is connected to the WAN transport which is typically connected to the Internet. Then, the Cisco edge platforms try to reach PnP server at devicehelper.cisco.com and uses an HTTPS connection to get the required information about the vBond, including the organization-name. After that, the vBond authenticates the device using its chassis/serial number and root certificate and provides the device with the vManage and vSmart controller information to the edge platform. Finally, the cEdge initiates and establishes secure connections with the vManage and vSmart controllers and downloads the configuration using NETCONF from vManage and joins the SD-WAN overlay network.
Zero-Touch Provisioning process
ZTP is as same as PnP provisioning process, though, it is for vEdge devices. In this process, vEdge devices try to connect to the ZTP server at ztp.viptela.com and uses an HTTPS connection to gather information about vBond orchestrator.
IOS XE SD WAN Bootstrap Deployment
This option is available only for IOS-XE SD-WAN WAN Edge platforms and not for vEdge devices. Leveraging bootstrap deployment requires the device template configuration to be built and attached to the WAN Edge device in vManage, after which the configuration file is built and shared with the WAN Edge device. Plus, the template file should be placed on the device flash memory with the ciscosdwan.cfg name on the ASR1K, ISR1K and ISR4K and ciscosdwan_cloud_init.cfg on the ASR1002-X devices. Then, on the boot up, the cEdge device learns the vBond and organization name from the system template embedded in the configuration and initiates a secure control connection to the vBond orchestrator. After successful authentication, the WAN Edge device receives information regarding the vManage and vSmart controllers and establishes secure connections with vManage and vSmart and downloads the entire configuration and joins the SD-WAN overlay network.
SD WAN Manual Deployment
For manual deployment, customers need to manually enter the whole configuration, such as System-IP, Site-ID, organization-name and vBond information and configure the transport VPN (VPN 0) interface with IP address, route and tunnel configuration.