Forti Secure SD-WAN
Organizations with a distributed infrastructure of remote offices and an expanding remote workforce must adapt as the use of business-critical cloud-based applications rises. The best solution is to switch from static, performance-restricted wide-area networks (WANs) to software-defined WAN (SD-WAN) architectures.
For all application and security requirements, traditional WANs may use leased line links or private MPLS with an SLA-backed SLA to an organization’s main data centers. However, the cost of connectivity is higher as a result. While a legacy hub-and-spoke architecture may offer centralized protection, it increases latency and reduces network performance for distributed cloud services for application access and computation. As a result, there is a lack of visibility and operational complexity related to numerous point products. This situation significantly increases management overhead and makes things more difficult, especially when trying to troubleshoot and fix problems.
By tightly integrating an organization’s network infrastructure and security architecture, Fortinet’s Security-driven Networking strategy enables networks to transform at scale without compromising security. By fusing a next-generation firewall with sophisticated SD-WAN networking capabilities, this new approach offers consistent security enforcement across adjustable perimeters. While improving user experience, this scheme does so without ever compromising on security. MPLS is no longer required for traffic backhaul. In addition to extending SD-WAN into branch offices’ wired and wireless access points, this integrated approach enables streamlined, single-console management for all networking and security requirements. Because of the increased integration of network security and controls, branch LAN networks can consistently enforce security.
Forti Secure SD-WAN fundamentals
The replacement of outdated hardware and software is only one aspect of SD-WAN modernization. Due to changes in how business users consume technology, organizations are implementing DX. Significant forces driving infrastructure evolution include device consolidation, cloud adoption, and cost savings from connectivity. Technology leaders frequently start WAN transformation projects because delivering a better user experience and increasing productivity are important goals. Branch locations with numerous points of connectivity to the internet or a corporate WAN can be benefited by SD-WAN solutions using control and data planes. The best path for a particular application is then selected from these. To ensure performance and maximize availability, data is transmitted over the best route.
With the help of WAN path failover, link aggregation, link remediation, and active path performance metrics, SD-WAN safeguards application availability and performance over corporate WANs and across the internet to multi-cloud environments. In essence, SD-WAN chooses which WAN path best meets performance requirements for a specific application and assigns packets or sessions to that WAN path.
By enabling direct internet access at the branch, a direct connection to a dynamic threat environment is also established. Branches with SD-WAN now require cutting-edge security capabilities at the network edge. Just giving someone direct internet access is insufficient.
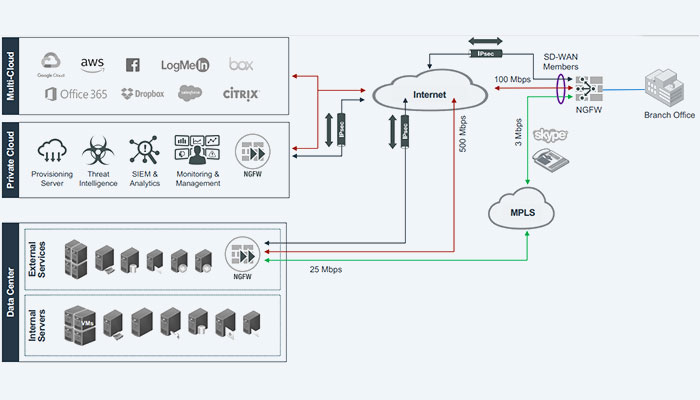
A redundant connectivity architecture is inherently provided for by direct internet access applied to an MPLS-based WAN. For critical applications that would typically only travel through the MPLS network, broadband offers an alternative path for data center connectivity.
Likewise, the internet broadband connection has supplanted the MPLS network as the means of access to the internet, though it will still be available.
Management and orchestration
Secure SD-WAN branch edge devices can be managed and coordinated centrally by the licensed Forti Secure SD-WAN. The FortiManager software used by an organization can be found there or in private or public clouds. No matter where it is, FortiManager keeps each FortiGate device connected, keeps track of performance SLAs, and provides a unified window into global connectivity. Additionally, it offers templates for setting up security policy, SD-WAN policy, and performance SLAs.
For complete deployment management, secure SD-WAN administrators only need FortiManager. the licensed Forti Secure SD-WAN adapts easily to the larger workflow within any organization thanks to its flexibility in supporting APIs and Security Fabric Connectors.
Forti Secure SD-WAN Business outcomes
Integrated Security on a Native Basis
To maintain the security and availability of the network, a built-in next-generation firewall (NGFW) combines the licensed Forti Secure SD-WAN and security capabilities into a single, integrated solution.
Operations Efficiency
Operations can be made easier with centralized orchestration, improved analytics, and SD-Branch at scale.
Increased Convergence
The industry’s only purpose-built, organically developed, and ASIC-powered SD-WAN enables thin edge (SD-WAN, routing) and WAN Edge (SD-WAN, routing, NGFW) to secure all applications, users, and data anywhere.
Enhancing the user experience
For improved network and application performance, an application-driven approach offers broad application steering with accurate identification, advanced WAN remediation, and accelerated cloud on-ramp.
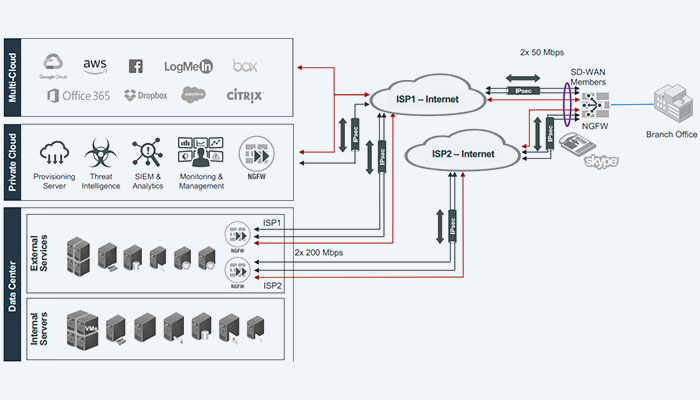
Paths over WAN (SD-WAN Interfaces)
The majority of the autonomous underlay and overlay interfaces that make up the licensed Forti Secure SD-WAN solution are combined into a single virtual WAN link.
On the branch FortiGate, there are four distinct interfaces defined. Two connections (WAN1 and WAN2) exist physically, one to the MPLS network and the other via the broadband provider. Two IPsec overlay interfaces, one for each physical underlay, have been developed by this organization. There are a total of four interfaces that can join the FortiGate virtual WAN link.
To increase bandwidth, this organization may decide to configure primary and secondary paths or even combine multiple paths. Any defined interface, whether underlay or overlay, may be a member of the SD-WAN virtual WAN link on the FortiGate NGFW. Inside the licensed Forti Secure SD-WAN, In accordance with x, each virtual domain (VDOM) may have a single SD-WAN virtual WAN link or SD-WAN interface. The design team should take inter-VDOM routing into consideration if an organization is thinking about implementing VDOMs at one or more branch sites to make sure the SD-WAN capabilities are utilizing multiple external WAN paths.
A minimum of two virtual WAN link member interfaces must be specified by administrators. Since FortiGate interfaces that are already referred to by a firewall policy or a static route cannot be added as member interfaces, SD-WAN configuration should be done as soon as FortiGate is set up.
Connections to a virtual private network
When deploying Secure SD WAN, VPN connections are essential. VPN tunnels occasionally exist as an overlay interface that multiplies the underlay interfaces.
Two underlay interfaces with the designations WAN1 and WAN2 are present in this type of network. This company has built four overlay interfaces for the FortiGate branch from these two interfaces. Using IPsec tunnels, the underlay interfaces are connected in a full mesh configuration. This particular organization may decide to add two underlay interfaces and four overlay interfaces for a total of six interfaces to the licensed Forti Secure SD-WAN virtual WAN link. From common hub and spoke and partial mesh to full mesh VPN architectures, FortiGate supports a wide range of connections for IPsec tunnels and architectures.
NGFW built-in
The integrated NGFW capabilities of the licensed Forti Secure SD-WAN are its most advantageous feature. Other solution architectures (e. g. tunneling to the cloud, offloading to third parties, etc. ), but WAN edge control and optimization are the main focuses of SD-WAN. As a result, it makes sense to exercise as much control at the edge as possible without going over budget. Both of these requirements are satisfied and exceeded by FortiGate.
The licensed Forti Secure SD-WAN is unmatched in terms of cost, performance, and security effectiveness because it offers a full range of SD-WAN and security functions at the branch edge before using expensive bandwidth. Examine the architecture of the FortiGate NGFW’s key features in relation to SD-WAN and WAN edge modernization.
The SOC3 offers the greatest value in every FortiGate appliance. To enable the fastest network security appliance currently available, these specially designed security processors dramatically increase performance and scalability. By preventing security from affecting network performance, this encourages organizations to keep up with the rapidly expanding bandwidth requirements. The packet processing and content scanning processes are partially accelerated by Fortinet security processors. Organizations can run numerous security applications simultaneously without experiencing performance degradation thanks to this tailored technology. An organization is able to run both SD-WAN and advanced security features on the same appliance for the same price (consolidation) and without experiencing performance degradation (OpEx savings).
Forti Secure SD-WAN Capabilities
- Promote digital transformation
- Application Recovery and Resilience
- Infrastructure for Integrated Security
- Consolidation of edge devices
- CapEx
- Reduced Complexity
- Longer response times
- Visibility of compliance behavior
- Aligning the security framework
- WAN Path Controller
- Awareness of the application
- Zero Touch Deployment
- Consolidating devices
- Enhanced WAN link performance
- Distribution of Dynamic Applications
- NGFW, or Next Generation Firewall
- Multiple Transport Support
- Managed Centrally
- Monitors with a single pane of glass
- Identity-based legislation
- SLAs (WAN Metrics)
- Traffic Management
- The WAN Path Controller
- Awareness of the application
- Zero-Touch Deployment
- Consolidating devices
- Enhanced WAN link performance
- Distributing dynamically
- Following Generation Firewall (NGFW)
- Support for multiple transports
- Management that is centralized
- Monitors with a single pane of glass
- Policy based on identity
- SLAs (WAN Metrics)
- Traffic Management