Tenable.sc Application
In order to precisely identify, research, and prioritize vulnerabilities on-premises, the Tenable.sc platform offers the most comprehensive and integrated view of your enterprise security posture. To manage and quantify your cyber risk, Tenable.sc, a market-leading vulnerability management solution, gives you visibility into your dynamic attack surface. The licensed Tenable.sc application assists you in determining which vulnerabilities to address first by providing advanced analytics, customizable dashboards, reports, and workflows. Tenable.sc also helps you understand your cyber risk. Based on cutting-edge Nessus technology, Tenable.sc compiles and analyzes vulnerability data from numerous Nessus scanners dispersed throughout your enterprise and displays vulnerability trends over time to assess risk and prioritize vulnerabilities.
Predictive Prioritization is a feature of Tenable.sc application that gathers information and threat intelligence from a variety of sources, analyzes it all using a data science algorithm that employs machine learning, and predicts the likelihood that a vulnerability will be exploited by threat actors. Learn which vulnerabilities to fix first and how to prioritize patching with real-time insight.
Tenable.sc application Key features
Visibility at all times
Track both known and unknown assets and their vulnerabilities continuously. Recognize threats and unforeseen network changes to prevent breaches.
Set Vulnerabilities in Priority
Utilize asset and vulnerability data, threat intelligence, and data science to create simple risk scores that can be quickly used to pinpoint the vulnerabilities and most vital assets that pose the greatest risk to the company.
Coverage in Both Breadth and Depth
The licensed Tenable.sc application Research closely collaborates with the security community to identify new vulnerabilities and to offer guidance to organizations as they develop their vulnerability assessment procedures. With more than 67K vulnerabilities, Tenable offers the most comprehensive CVE and security configuration support in the market to help you understand all of your exposures.
Streamline procedures
Use a fully documented API and pre-built integrations to share data with your IT systems, automate scans, and import data from third parties.
Tenable.sc application Key Capabilities
Tenable Research
With support from Tenable Research, Tenable.sc provides top-notch Cyber Exposure intelligence, data science insights, alerts, and security advisories. The most recent vulnerability assessments, zero-day investigations, and configuration benchmarks are constantly available to you so you can secure your organization thanks to Tenable Research’s frequent updates.
Use Director from Tenable.com
The licensed Tenable.sc application director is an add-on that gives you complete visibility across all of your consoles for your entire deployment and centralized management of your risk posture.
Pre-Built Integrations, a Known API, and an Integrated SDK
You can easily automate your vulnerability management process with Tenable.sc’s out-of-the-box integrations for credentialed scanning, SIEM, SOAR, ticketing and patching systems, and other complementary solutions. This page includes a comprehensive list. Tenable.sc also offers a fully documented API that you can use to easily build your own integrations with. Utilizing these tools will help you get the most out of your individual vulnerability management use cases at no additional cost.
Prioritization of Vulnerabilities Based on Actual Risk
The licensed Tenable.sc application combines vulnerability information with threat intelligence and data science to produce a risk score that is simple to understand and helps you prioritize which vulnerabilities to fix first. Rapid risk assessment and vulnerability identification with the greatest organizational impact are possible.
Vulnerability management made easier
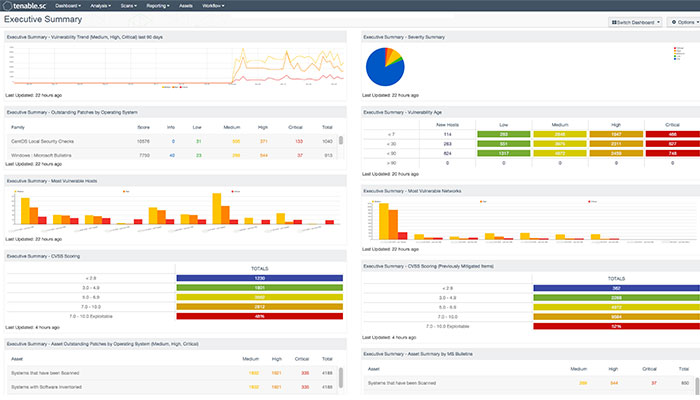
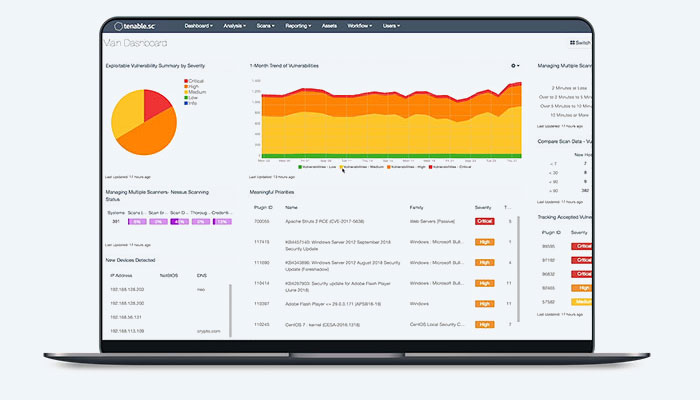
Tenable.sc streamlines routine tasks like setting up scans, executing assessments, and analyzing results with intuitive reports, dashboard visualizations, and an easy-to-use interface. You can protect your organization with a fraction of the work otherwise required by using predefined scan templates, configuration audit checks, and compliance audit checks that adhere to best practices frameworks. Utilize pre-configured, out-of-the-box dashboards to tailor your reporting and analysis, or quickly create your own from scratch to suit organizational requirements
Simplified Compliance
Recognize compliance with pre-established checks, metrics, and proactive alerts on violations for industry standards and legal requirements, and report on compliance. There are numerous industry standards, such as CERT, NIST, DISA STIG, DHS CDM, FISMA, PCI DSS, and HIPAA/HITECH.
Take control of your data
The best on-premises solution for vulnerability management is provided by Tenable.sc. Manage your data the way you want to with on-premises or hybrid deployment options that fit your most complex deployment needs while lowering organizational risk.
Options for a thorough assessment
Your entire attack surface is visible to you at once thanks to Tenable.sc. It makes use of Nessus Sensors, a combination of active scanners, agents, passive network monitoring, and CMDB integrations, to maximize scan coverage across your infrastructure and lessen vulnerability blind spots. This variety of data sensor types enables you to monitor and evaluate the vulnerabilities of both known and unidentified assets.
Discovering Passive Assets
Find and recognize the IT assets that are connected to your network, such as servers, desktops, laptops, network devices, web applications, virtual machines, mobile devices, and cloud.
Deployments in stages
Data sharing between various Tenable.sc instances is accomplished using a tiered remote repository configuration.
- Tenable suggests setting up a tiered remote repository configuration if you intend to support 100,000–24 9,999 hosts.
- A tiered remote repository configuration is required by Tenable if you intend to support 250,000 or more hosts.
In your overall deployment of Tenable.sc, tiered instances play unofficial roles. For every 100,000 to 150,000 hosts on your network, Tenable advises installing at least one designated reporting Tenable.sc instance as well as an additional Tenable.sc instance.
- A scanning tier from The licensed Tenable.sc application manages scan jobs across your attached scanners to optimize scanning. Effective scan data collection is prioritized by scanning tier Tenable.sc instances.
- The data gathered by scanning tier Tenable.sc instances is centrally stored in a reporting tier Tenable.sc, which optimizes dashboards and reporting.
Controlling access
The RBAC principles are supported by the Tenable.sc user access model. Users on a team can access the same data (by shared group) with varying levels of access (by role) to carry out various tasks because each user has a defined group membership (for data access) and role (for application access). An assortment of groups and the users within them are contained in organizations that you configure.
Organizations permit a distinct set of users and groups, each with their own set of resources. With the help of this functionality, you can replicate the organizational structure of your business in Tenable.sc.
You could, for illustration:
- A Senior Vulnerability Management Engineer should be given full access to Security Manager.
- C-level executives should not be given access, but security managers should be told to export and share ARCs instead.
- Authorize a Security Engineer to export API data.
- Give a Security Engineer access to API integrations.
Network Scan Coverage
It can be challenging to get a clear picture (and total number) of the assets on your network because the majority of organizations use a variety of technological platforms. Your network may contain resources that serve a variety of infrastructure, operating system, software, and hardware needs.
The majority of Tenable.sc data, scans, queries, and reports are based on asset IP addresses. The licensed Tenable.sc application is primarily an IP address-based tool. When addressing network size and licensing, the IP address count of the resources on your network serves as the primary gauge of information.
When deploying Tenable.sc for the first time, you should think about supporting more assets on your network than you are currently tracking. Tenable typically advises increasing your total by 20–30% to account for previously unseen assets. The precise increase varies, but a range of 20 to 30 percent is a good place to start when determining the size of your network.
Active Scanners
If you plan to use active scanning, keep in mind that Nessu
s scanner deployments are made to be adaptable to the particular requirements of your network architecture. Nessus coverage can be improved in many different ways. You could configure, as an example:
- An isolated, low-bandwidth network area with 50 IP addresses is covered by a single scanner that is dedicated to that scan zone.
- A flat network area with 50,000 IP addresses is covered by ten scanners that are each dedicated to a number of scan zones.