Vulnerability Management Using Tenable
Security and audit teams can share an unlimited number of users or groups’ scan schedules, scan policies, and scan results among multiple Nessus, Nessus Agent, and Nessus Network Monitor scanners.
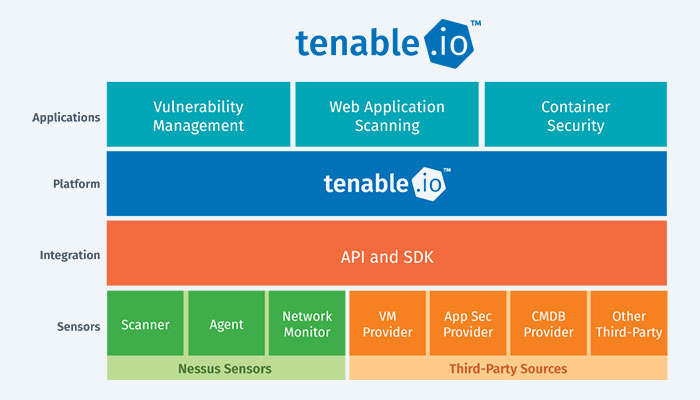
The licensed Tenable One is an exposure management platform that enables businesses to accurately communicate cyber risk, gain visibility across the modern attack surface, and concentrate defenses against likely attacks.
In addition to leveraging Tenable Research’s speed and breadth of vulnerability coverage, the platform combines the most comprehensive vulnerability coverage across IT assets, cloud resources, containers, web apps, and identity systems. It also adds extensive analytics to prioritize actions and communicate cyber risk. Businesses can: with Tenable One:
- Make better decisions by communicating cyber risk.
- Obtain complete awareness of the contemporary attack surface.
- Be aware of potential dangers and concentrate your efforts on preventing attacks.
The licensed Tenable can be purchased separately or as a component of the Tenable One Exposure Management platform.
You can use Tenable for Vulnerability Management
Companies and organizations can use Tenable for Vulnerability Management by following these steps:
- Review principles of the TCP/IP internet protocol suite. The documentation for Tenable makes the assumption that you are familiar with the fundamental ideas and concepts of networking.
- Your Tenable representative can provide you with your Tenable access information and starter account credentials.
- Access Tenable Support and training materials for Tenable, such as the Professional Services Scan Strategy, as needed.
- Determine your organization’s goals and examine your network topology before creating a deployment strategy. Take into account the best practices that Tenable recommends for your environment.
- Create a plan for internal and external scanning. Determine the scans you want to perform, and make sure your network is sufficiently covered.
- Create a process for analysis. Consider the data you intend to share with each stakeholder when identifying the key stakeholders in your management and operational groups.
Vulnerability Management Licensing
The maximum number of assets you can scan for vulnerabilities in with the licensed Tenable Vulnerability Management is determined by the licensed asset limit. If your license usage goes over the allotted amount, you can still scan your assets using Tenable while waiting for the license to be adjusted as necessary.
Risk Assessment and Management
You can check your environment for vulnerabilities with Tenable. The licensed Tenable, in contrast to Nessus and Tenable, is hosted in the cloud and enables remote scanning using your Nessus scanners and Nessus Agents or Tenable cloud scanners if you want to scan assets from an outside network.
Nessus Scanner and Nessus Agent scan templates from Tenable Vulnerability Management are offered in a variety of formats to accommodate various business requirements. Tenable Vulnerability Management offers four types of scan templates: vulnerability scans, configuration scans, tactical scans, and inventory collection. When you Create a Vulnerability Management Scan in the user interface, you can see the full selection of scan templates offered by Tenable Vulnerability Management.
Vulnerability scans
For the majority of your company’s standard, everyday scanning requirements, Tenable advises using vulnerability scan templates. The following are a few of the most notable vulnerability scan templates from Tenable
Comprehensive Network/Agent Scan
The licensed Tenable Vulnerability Management’s most customizable scan type. This scan template can be modified to comply with any policy.
Network/Agent Scan in the Basics
Utilize this template to scan assets while all of Tenable active plugins are active. This scan offers an efficient method for checking assets for all vulnerabilities.
Patch audit with credentials (only for Nessus Scanner)
This template can be used to grant the scanner direct access to the host so that it can scan the target hosts and list any missing patch updates.
The Nessus Scanner is the only host discovery
Start this scan to discover the hosts that are present on your network and any relevant details, such as IP addresses, FQDNs, operating systems, and open ports, if any. The hosts you want to focus on in a particular vulnerability scan can be chosen once you have a list of all the hosts.
The licensed Tenable advises businesses without passive network monitors, like Nessus Network Monitor, to run this scan once a week to find new assets on their network.
(Only using a Nessus Scanner) Tactical scans
You can scan your assets for a specific vulnerability using tactical scans, which are quick, light-weight scan templates. The licensed Tenable Tactical Scans library is regularly updated by Tenable with templates that find the most recent security flaws of interest to the general public, like Log4Shell.
Inventory Take-Up (Only for Nessus Agent)
The Collect Inventory template utilizes Tenable’s Frictionless Assessment technology in contrast to standard Nessus Agent vulnerability scans to deliver faster scan results and minimize the scan’s system footprint.
The majority of Tenable Vulnerability Management scan templates are designed to produce assessment scans, which are scans that identify vulnerabilities on your assets. The ability to create discovery scans—scans that locate resources on your network—is provided by a few of the scan templates, including Host Discovery.