Cisco TrustSec
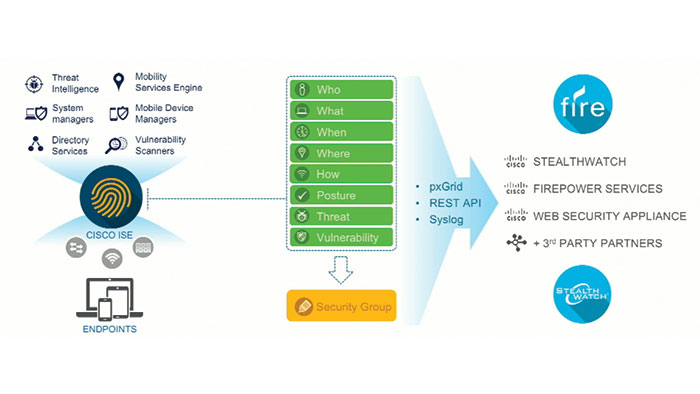
Cisco TrustSec is an effective and open software-defined segmentation technology that simplifies access control. With TrustSec, controls are defined using endpoint rolls, not IP addresses. Essentially, its human-friendly logical groups are more flexible, and much easier to manage than IP address based controls. TrustSec makes it easy to configure new groups or users without disrupting current groups. By simplify adding a column to the TrustSec Policy Matrix within Cisco Identify Services Engine, for ISE, you can define the selected group and adds it to your policy in minutes. Meanwhile, another serious issue crops up. With Cisco TrustSec, your network has already restricted the lateral movement of the threat. TrustSec enabled devices like firewalls, IPS, and ISE, works together to isolate the infected system itself. The security centers in your network will be continuously scanning for suspicious activity and when a threat is detected, the admins will be notified at once. At the same time, ISE changes the group membership of the suspicious device and automatically quarantines it. It all adds up to faster security and more efficient IT for your company.
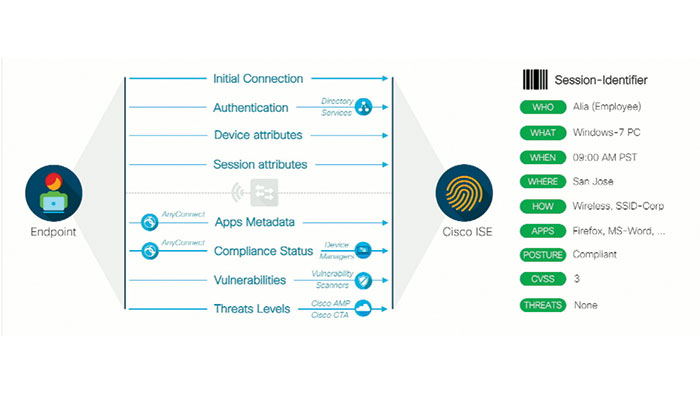
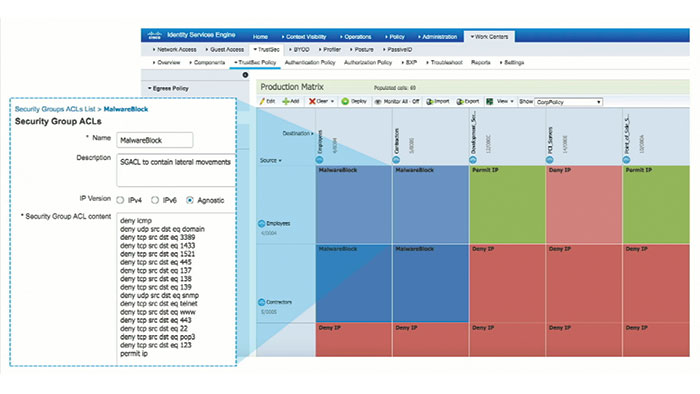
Cisco TrustSec builds security and intelligence into the network with policy based access control, identity aware networking, data confidentiality and data integrity. Basically, TrustSec is role-based, this means for every user and device on the network, you must stablish what their job is. In order to do that, TrustSec first starts with making your network role-aware. Cisco TrustSec is designed to use the network devices that you already have and since the role enforcement is actually is done at the device level, the first step for TrustSec deployment is to authenticate the device itself within the TrustSec framework. This identifies all legitimate devices or roles on your network with the express purposes of keeping rogue devices from entering and being used as an attack vector. At once your infrastructure is authenticated, you need to look at two key concepts: Security Group Tags (SGTs) and Security Group Access Control Lists (SGACL).
Briefly, SGACLs are the enforcement arm of TrustSec and the advantage of that over plain ACL, is that they do not use IP addresses. In addition, SGT is a unique 16-bit tag assigned to each individual role and device that connects it to a TrustSec domain. The Tag itself indicates a privilege level across entire domain. Therefore, an SGT is passed along dynamically to a switch or an access point, after either the 802.1X. the web authentication or the MAC authentication bypass which would happen with RADIUS vendor specific attribute. SGTs dynamically automate the process of network-wide policy deployment and enforcement. So instead of manually typing entries into an ACL, you can benefit from a security policy change. This innovation is going to spare a lot of times.
Moreover, to ensure confidentiality and integrity, there is also hop-by-hop encryption based on 802.1AE is available to complete TrustSec deployment. So if the frames are being captured, no information would be leaked. Packets are encrypted on egress and decrypt it on ingress.