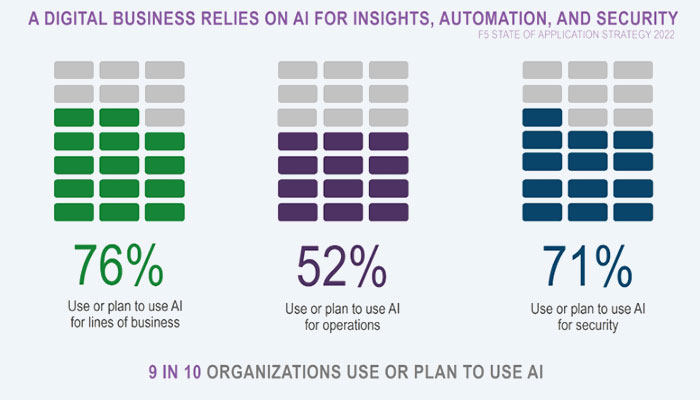
Artificial Intelligence using Big-IQ
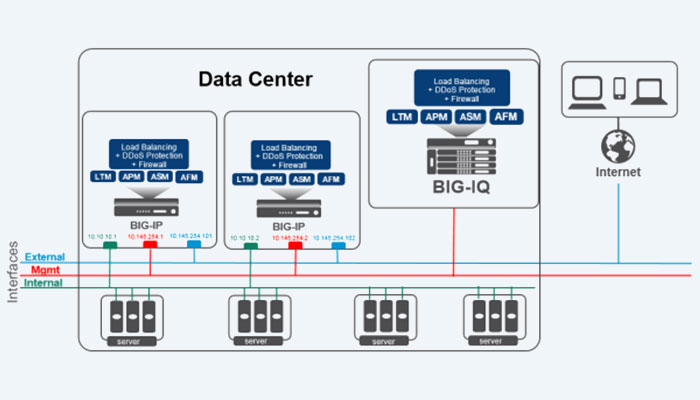
By offering a centralized management interface for all of your BIG-IP devices, whether they are on-site or in a public or private cloud, BIG-IQ helps you save time and money or block frauds with Artificial Intelligence powered Solutions. Any BIG-IP device, whether physical or virtual, may be managed as long as layer 3 connectivity can be established for management via a graphical user interface (GUI) or APIs. On AWS, Azure, and the majority of private cloud architectures, BIG-IQ can be used.
The licensed BIG-IQ represents various application services that support an app as a single entity in order to further clarify and simplify app management. You can visualize and manage the aggregation of these services to get a complete view across various environments, tiers, or geographies by combining services into a single application.

Including those set up with the Application Services 3 Extension (AS3), this enables improved management capabilities for all DNS, TCP, and HTTP instances of an application deployment. The user access and management privileges for these application deployments can be set by the system administrator. By providing deep visibility into the health and performance of your applications as well as simple, unified operations, BIG-IQ assists teams in adjusting to the flexibility of the cloud. This allows you to make data-driven decisions and react quickly to changes in application environments, which are highly variable.
Access control based on roles
In order for an organization to operate at the speed of innovation, each employee must perform their duties well. Role-based access control (RBAC) is essential not only for security reasons but also for carrying out daily tasks effectively. The licensed BIG-IQ supports fine-grained, highly customizable RBAC, allowing security and application teams to manage their own application services, policies, and configurations without relying on network administrators.
Manage who can view application dashboards, edit and deploy services and policies for application delivery and security, and deploy your own roles and permissions configurations using the predefined BIG-IQ roles and permissions configurations. Users and groups from nearby Active Directory (AD), TACACS, RADIUS, or LDAP servers can be linked to roles, as can users and groups from other locations.
Additionally, as F5 releases new versions of BIG-IQ using Artificial Intelligence technology, RBAC will be expanded to more workflows, dashboards, logs, and reports, ensuring that every BIG-IQ user has the proper visibility into and control over their area of the application.
Centralized Analytics Logs
Your F5 application delivery and security portfolio can be analyzed for health, performance, and availability in any environment using BIG-IQ`s Artificial Intelligence (AI) powered technologies, a single, end-to-end solution. It offers thorough analytics, logging, and auditing across all supported devices, services, and applications, making it simple to guarantee consistency across hybrid and multi-cloud deployments and streamline troubleshooting in the event that something goes wrong.
Deep, application-centric analytics are what drive this comprehensive perspective. Analytics are gathered by the data collection devices from BIG-IQ. Data Collection Devices are a free and unlicensed part of the BIG-IQ solution. When performance and health metrics are recorded using a data collection device, they are shown on the highly individualized dashboards of the licensed BIG-IQ that can:
- Provide information on the state of security, server side round trip time, a particular browser’s performance, and a wide range of other useful metrics.
- Extend visibility, analytics, and fundamental configuration controls to legacy app services (deployed without a template or using BIG-IQ).
- Deep views of the health and performance of the app that are specific to the application and the role.
- Display high-level analytics and “at-a-glance” status.
A solution powered by Artificial Intelligence that protects users’ online experiences while preventing fraud that is missed by current technologies.
To try to catch fraudsters who are getting smarter all the time, traditional fraud tools rely on flimsy data signals and rigid rules. These tools frequently struggle to tell whether a user has good or bad intentions, and as a result, they force good users to go through extra hoops like multi-factor authentication (MFA) challenges in order to establish their legitimacy. Bad user experiences, financial losses, and frustration arise as a result of fraudsters circumventing ineffective security measures.
The friction for known good users of SAFE, on the other hand, is reduced by up to 90% while fraudsters are stopped in real time thanks to Artificial Intelligence technology. SAFE protects both modern and traditional applications as a fully managed service that can identify and thwart evolving threats. This enables businesses to accelerate their digital initiatives and lessen the frequently excessive workload on fraud teams.
What can Artificial Intelligence using Big-IQ do?
In the following ways, SAFE overcomes the issues facing the industry today:.
Helps fraud teams work more effectively
SAFE is delivered as a fully managed service, with ongoing tuning carried out by Shape fraud experts, and actively blocks fraud without requiring fraud teams to write or maintain rules. Additionally, SAFE saves fraud teams time and resources by preventing fraud at the application perimeter rather than requiring them to conduct manual investigations. For one client, SAFE discovered that 67% of fraud cases could be effectively blocked without being looked into. Another example: In a six-week period, SAFE discovered 33,000 fraudulent transactions that could be blocked rather than investigated.
For actual customers, reduces friction
Because their current fraud tools can’t effectively distinguish between legitimate customers and fraudsters, organizations and application owners may impose friction on legitimate users out of fear of fraud. By safely removing MFA challenges for known good users, SAFE significantly lowers friction on legitimate activity by combining proprietary telemetry and cutting-edge AI.
Stops fraud more quickly
When a user creates a new account, logs in, completes a transaction, sends a payment, or takes any other action, SAFE detects fraudulent transactions throughout the entire user journey. In addition to having the intelligence to support applications in scaling and adapting performance, security, and other crucial services as necessary, SAFE uses Artificial Intelligence to accurately detect and block malicious intent. SAFE typically detects twice as much fraud each month as other fraud detection tools. One significant North American bank found 250 percent more account takeover fraud with SAFE than with their current tools in 60 days, preventing an additional $10M in fraud losses annually.
Automation
Utilize the AS3 and BIG-IQ to manage your applications. Consistent BIG IP application services and policies can be easily created, configured, and deployed quickly and easily thanks to AS3 and BIG-IQ. When deploying application services, you can use AS3 templates that you can create, import, and edit using a declarative model thanks to this integration.
When you combine BIG-IQ with AS3’s declarative API and templated approach, you can support standardized, automated declarative app services and security policies. This allows you to hasten application deployment, guarantee consistency, and boost deployment flexibility without requiring specialized domain knowledge. Reusability of AS3 declarations ensures repeatability and reduces manual repetition for numerous service deployments. While development teams continue to make use of the API they already know and love, NetOps teams can use AS3 in BIG-IQ by utilizing an easy-to-use GUI. It is now simpler than ever to automate and centrally manage advanced application services as part of the F5 Automation Toolchain thanks to the licensed BIG-IQ and AS3 integration.
You can find templates in the AS3 template library for BIG IQ maintained by F5 that you can use as-is or modify for your deployment environment. The templates can be downloaded right to your licensed BIG-IQ system. The templates can be used just like any other AS3 application template once you download them. Similar to how they operate on BIG-IP, AS3 templates operate on BIG-IQ.
Access
The licensed BIG-IQ employs RBAC to divide up operational responsibilities, cut down on management blunders, and shorten downtime. Whether your applications are hosted locally or in the cloud, it also enables you to manage a trustworthy, efficient security posture across deployments. With the licensed BIG-IQ, you can use declarative REST API-driven workflows to manage and monitor BIG-IP APM and Secure Web Gateway appliances as well as Secure Web Gateway as an SSL Orchestrator service, which makes the process quicker, more repeatable, and in line with contemporary application development and deployment practices.
The Visual Policy Editor facilitates comprehension and management of access security (e. g. Policies for VPNs, SSO, and Federations. Additionally, you get a ton of reporting tools for your SSL VPN, VDI, users, web access application usage, and Secure Web Gateway operations. Additionally, you can deploy and import policy configurations to apply access control policies across BIG-IP APM instances, and enable OpenID Connect (OIDC) with session variables to confirm user identities when using HTTPS endpoints (BIG-IP 16.1 and higher). Additionally, it enables you to make sure that your entire IT infrastructure complies with policy.